1. 安装 BIND 服务器软件并启动
yum -y install bind bind-utils systemctl start named.service // 启动服务 systemctl enable named // 设为开机启动yum -y install bind bind-utils systemctl start named.service // 启动服务 systemctl enable named // 设为开机启动yum -y install bind bind-utils systemctl start named.service // 启动服务 systemctl enable named // 设为开机启动
1.1. 查看named进程是否正常启动
ps -eaf|grep named // 检查进程 ss -nult|grep :53 // 检查监听端口ps -eaf|grep named // 检查进程 ss -nult|grep :53 // 检查监听端口ps -eaf|grep named // 检查进程 ss -nult|grep :53 // 检查监听端口
如图:
[root@localhost named]# ss -nltp |grep :53 LISTEN 0 10 192.168.1.194:53 *:* users:(("named",pid=29998,fd=24)) LISTEN 0 10 127.0.0.1:53 *:* users:(("named",pid=29998,fd=21)) LISTEN 0 10 172.17.0.1:53 *:* users:(("named",pid=29998,fd=23)) LISTEN 0 10 ::1:53 :::* users:(("named",pid=29998,fd=22))[root@localhost named]# ss -nltp |grep :53 LISTEN 0 10 192.168.1.194:53 *:* users:(("named",pid=29998,fd=24)) LISTEN 0 10 127.0.0.1:53 *:* users:(("named",pid=29998,fd=21)) LISTEN 0 10 172.17.0.1:53 *:* users:(("named",pid=29998,fd=23)) LISTEN 0 10 ::1:53 :::* users:(("named",pid=29998,fd=22))[root@localhost named]# ss -nltp |grep :53 LISTEN 0 10 192.168.1.194:53 *:* users:(("named",pid=29998,fd=24)) LISTEN 0 10 127.0.0.1:53 *:* users:(("named",pid=29998,fd=21)) LISTEN 0 10 172.17.0.1:53 *:* users:(("named",pid=29998,fd=23)) LISTEN 0 10 ::1:53 :::* users:(("named",pid=29998,fd=22))
1.2. 开放 TCP 和 UDP 的 53 端口
firewall-cmd --permanent --add-port=53/tcp firewall-cmd --permanent --add-port=53/udp firewall-cmd --reload // 重新加载防火墙配置,让配置生效firewall-cmd --permanent --add-port=53/tcp firewall-cmd --permanent --add-port=53/udp firewall-cmd --reload // 重新加载防火墙配置,让配置生效firewall-cmd --permanent --add-port=53/tcp firewall-cmd --permanent --add-port=53/udp firewall-cmd --reload // 重新加载防火墙配置,让配置生效
2. DNS 服务的相关配置文件
2.1. 修改主要文件 /etc/named.conf
修改前先备份: cp -p /etc/named.conf /etc/named.conf.bak // 参数-p表示备份文件与源文件的属性一致。
修改配置:vi /etc/named.conf , 配置内容如下:
options { listen-on port 53 { any; }; listen-on-v6 port 53 { any; }; directory "/var/named"; dump-file "/var/named/data/cache_dump.db"; statistics-file "/var/named/data/named_stats.txt"; memstatistics-file "/var/named/data/named_mem_stats.txt"; allow-query { any; }; /* - If you are building an AUTHORITATIVE DNS server, do NOT enable recursion. - If you are building a RECURSIVE (caching) DNS server, you need to enable recursion. - If your recursive DNS server has a public IP address, you MUST enable access control to limit queries to your legitimate users. Failing to do so will cause your server to become part of large scale DNS amplification attacks. Implementing BCP38 within your network would greatly reduce such attack surface */ recursion yes; dnssec-enable yes; dnssec-validation yes; /* Path to ISC DLV key */ bindkeys-file "/etc/named.iscdlv.key"; managed-keys-directory "/var/named/dynamic"; pid-file "/run/named/named.pid"; session-keyfile "/run/named/session.key"; }; logging { channel default_debug { file "data/named.run"; severity dynamic; }; }; zone "." IN { type hint; file "named.ca"; }; include "/etc/named.rfc1912.zones"; include "/etc/named.root.key";options { listen-on port 53 { any; }; listen-on-v6 port 53 { any; }; directory "/var/named"; dump-file "/var/named/data/cache_dump.db"; statistics-file "/var/named/data/named_stats.txt"; memstatistics-file "/var/named/data/named_mem_stats.txt"; allow-query { any; }; /* - If you are building an AUTHORITATIVE DNS server, do NOT enable recursion. - If you are building a RECURSIVE (caching) DNS server, you need to enable recursion. - If your recursive DNS server has a public IP address, you MUST enable access control to limit queries to your legitimate users. Failing to do so will cause your server to become part of large scale DNS amplification attacks. Implementing BCP38 within your network would greatly reduce such attack surface */ recursion yes; dnssec-enable yes; dnssec-validation yes; /* Path to ISC DLV key */ bindkeys-file "/etc/named.iscdlv.key"; managed-keys-directory "/var/named/dynamic"; pid-file "/run/named/named.pid"; session-keyfile "/run/named/session.key"; }; logging { channel default_debug { file "data/named.run"; severity dynamic; }; }; zone "." IN { type hint; file "named.ca"; }; include "/etc/named.rfc1912.zones"; include "/etc/named.root.key";options { listen-on port 53 { any; }; listen-on-v6 port 53 { any; }; directory "/var/named"; dump-file "/var/named/data/cache_dump.db"; statistics-file "/var/named/data/named_stats.txt"; memstatistics-file "/var/named/data/named_mem_stats.txt"; allow-query { any; }; /* - If you are building an AUTHORITATIVE DNS server, do NOT enable recursion. - If you are building a RECURSIVE (caching) DNS server, you need to enable recursion. - If your recursive DNS server has a public IP address, you MUST enable access control to limit queries to your legitimate users. Failing to do so will cause your server to become part of large scale DNS amplification attacks. Implementing BCP38 within your network would greatly reduce such attack surface */ recursion yes; dnssec-enable yes; dnssec-validation yes; /* Path to ISC DLV key */ bindkeys-file "/etc/named.iscdlv.key"; managed-keys-directory "/var/named/dynamic"; pid-file "/run/named/named.pid"; session-keyfile "/run/named/session.key"; }; logging { channel default_debug { file "data/named.run"; severity dynamic; }; }; zone "." IN { type hint; file "named.ca"; }; include "/etc/named.rfc1912.zones"; include "/etc/named.root.key";
named-checkconf // 检查named.conf是否有语法问题named-checkconf // 检查named.conf是否有语法问题named-checkconf // 检查named.conf是否有语法问题
2.2. 配置正向解析和反向解析
2.2.1. 修改/etc/named.rfc1912.zones
添加配置: vi /etc/named.rfc1912.zones , 配置内容如下:
zone "ldky.xyz" IN { type master; file "ldky.xyz"; allow-update { none; }; }; zone "1.168.192.in-addr.arpa" { type master; file "192.168.1"; allow-update { none; }; };zone "ldky.xyz" IN { type master; file "ldky.xyz"; allow-update { none; }; }; zone "1.168.192.in-addr.arpa" { type master; file "192.168.1"; allow-update { none; }; };zone "ldky.xyz" IN { type master; file "ldky.xyz"; allow-update { none; }; }; zone "1.168.192.in-addr.arpa" { type master; file "192.168.1"; allow-update { none; }; };
2.2.2. 添加正向解析域
基于 name.localhost 模板,创建配置文件:cp -p /var/named/named.localhost /var/named/ldky.xyz
配置正向域名解析文件 ldky.xyz : vi /var/named/ldky.xyz ,配置内容如下:
$TTL 1D @ IN SOA @ ldky.xyz. ( 0 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum @ IN NS dns1.ldky.xyz. dns1 IN A 192.168.1.66 jyy IN A 192.168.1.90 www IN CNAME jyy.ldky.xyz.$TTL 1D @ IN SOA @ ldky.xyz. ( 0 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum @ IN NS dns1.ldky.xyz. dns1 IN A 192.168.1.66 jyy IN A 192.168.1.90 www IN CNAME jyy.ldky.xyz.$TTL 1D @ IN SOA @ ldky.xyz. ( 0 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum @ IN NS dns1.ldky.xyz. dns1 IN A 192.168.1.66 jyy IN A 192.168.1.90 www IN CNAME jyy.ldky.xyz.
说明:
- jyy.ldky.xyz 将会解析为 192.168.1.90
检查区域文件是否正确 named-checkzone "ldky.xyz" "/var/named/ldky.xyz" ,如图:
[root@localhost named]# named-checkzone "ldky.xyz" "/var/named/ldky.xyz" zone ldky.xyz/IN: loaded serial 0 OK[root@localhost named]# named-checkzone "ldky.xyz" "/var/named/ldky.xyz" zone ldky.xyz/IN: loaded serial 0 OK[root@localhost named]# named-checkzone "ldky.xyz" "/var/named/ldky.xyz" zone ldky.xyz/IN: loaded serial 0 OK
2.2.3. 添加反向解析域
基于 name.localhost 模板,创建配置文件: cp -p /var/named/named.localhost /var/named/192.168.1
配置反向域名解析文件 192.168.1 : vi /var/named/192.168.1
$TTL 1D @ IN SOA @ ldky.xyz. ( 0 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum @ IN NS dns1.ldky.xyz. 66 IN PTR dns1.ldky.xyz. 90 IN PTR jyy.ldky.xyz.$TTL 1D @ IN SOA @ ldky.xyz. ( 0 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum @ IN NS dns1.ldky.xyz. 66 IN PTR dns1.ldky.xyz. 90 IN PTR jyy.ldky.xyz.$TTL 1D @ IN SOA @ ldky.xyz. ( 0 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum @ IN NS dns1.ldky.xyz. 66 IN PTR dns1.ldky.xyz. 90 IN PTR jyy.ldky.xyz.
检查区域文件是否正确 named-checkzone "1.168.192.in-addr.arpa" "/var/named/192.168.0" ,如图:
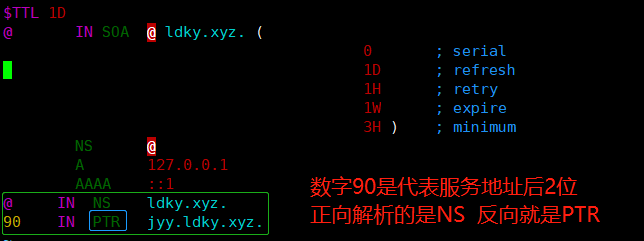
[root@localhost named]# named-checkzone "1.168.192.in-addr.arpa" "/var/named/192.168.1" zone 1.168.192.in-addr.arpa/IN: loaded serial 0 OK[root@localhost named]# named-checkzone "1.168.192.in-addr.arpa" "/var/named/192.168.1" zone 1.168.192.in-addr.arpa/IN: loaded serial 0 OK[root@localhost named]# named-checkzone "1.168.192.in-addr.arpa" "/var/named/192.168.1" zone 1.168.192.in-addr.arpa/IN: loaded serial 0 OK
2.2.4. 重启 named 服务,让配置生效
重启 named 服务,让配置生效 systemctl restart named
2.named 命令允许动态更新
rndc reload
3. 在 Linux 下的 DNS 客户端的设置及测试
3.1. 注册域名解析服务器到配置文件
配置 ifcfg-ens192 vim /etc/sysconfig/network-scripts/ifcfg-ens192
DNS2=192.168.1.66DNS2=192.168.1.66DNS2=192.168.1.66
重启网络服务,让配置生效 systemctl restart network.service
或者更改/etc/resolv.conf DNS配置文件(重启网卡之后配置会还原)
# Generated by NetworkManager search ldky.xyz nameserver 192.168.1.66# Generated by NetworkManager search ldky.xyz nameserver 192.168.1.66# Generated by NetworkManager search ldky.xyz nameserver 192.168.1.66
3.2. 使用 nslookup 测试
bind-utils 软件包本身提供了测试工具 nslookup
3.3.1. 正向域名解析测试
nslookup jyy.ldky.xyz , 或者,如下图:
[root@localhost named]# nslookup jyy.ldky.xyz Server: 192.168.1.66 Address: 192.168.1.66#53 Name: jyy.ldky.xyz Address: 192.168.1.90[root@localhost named]# nslookup jyy.ldky.xyz Server: 192.168.1.66 Address: 192.168.1.66#53 Name: jyy.ldky.xyz Address: 192.168.1.90[root@localhost named]# nslookup jyy.ldky.xyz Server: 192.168.1.66 Address: 192.168.1.66#53 Name: jyy.ldky.xyz Address: 192.168.1.90
3.3.2. 反响域名解析测试
nslookup 192.168.0.90 , 或者,如下图:
[root@localhost named]# nslookup 192.168.1.90 90.1.168.192.in-addr.arpa name = jyy.ldky.xyz.[root@localhost named]# nslookup 192.168.1.90 90.1.168.192.in-addr.arpa name = jyy.ldky.xyz.[root@localhost named]# nslookup 192.168.1.90 90.1.168.192.in-addr.arpa name = jyy.ldky.xyz.
部署完成
原文链接:https://blog.csdn.net/m0_57480266/article/details/120350970?ops_request_misc=&request_id=&biz_id=&utm_medium=distribute.pc_search_result.none-task-blog-2~blog~koosearch~default-29-120350970-null-null.268%5Ev1%5Ekoosearch&utm_term=%E9%BB%91%E7%BE%A4%E6%99%96%E3%80%81docker%E3%80%81%E5%AE%B9%E5%99%A8%E9%95%9C%E5%83%8F%E3%80%81%E5%9F%9F%E5%90%8D%E6%B3%A8%E5%86%8C%E3%80%81%E5%AE%9D%E5%A1%94%E3%80%81%E5%8F%8D%E5%90%91%E4%BB%A3%E7%90%86%E3%80%81nginx%E3%80%81frp%E3%80%81%E5%8A%A8%E6%80%81%E5%9F%9F%E5%90%8D%E8%A7%A3%E6%9E%90%E3%80%81NAS%E3%80%81%E7%BE%A4%E6%99%96%E3%80%81%E9%98%BF%E9%87%8C%E4%BA%91%E3%80%81%E5%9F%9F%E5%90%8D%E8%A7%A3%E6%9E%90%E3%80%81%E5%86%85%E7%BD%91%E7%A9%BF%E9%80%8F%E3%80%81ipv6%E3%80%81ddns%E3%80%81%E8%BD%BB%E9%87%8F%E7%BA%A7%E4%BA%91%E6%9C%8D%E5%8A%A1%E5%99%A8%E3%80%81%E9%93%81%E5%A8%81%E9%A9%AC%E3%80%81%E5%A8%81%E8%81%94%E9%80%9A%E3%80%81DSM%E3%80%81DSM6.0%E3%80%81%E7%BE%A4%E6%99%96nas%E3%80%81%E4%BA%91%E6%9C%8D%E5%8A%A1%E5%99%A8%E3%80%81%E8%9C%97%E7%89%9B%E6%98%9F%E9%99%85%E3%80%81