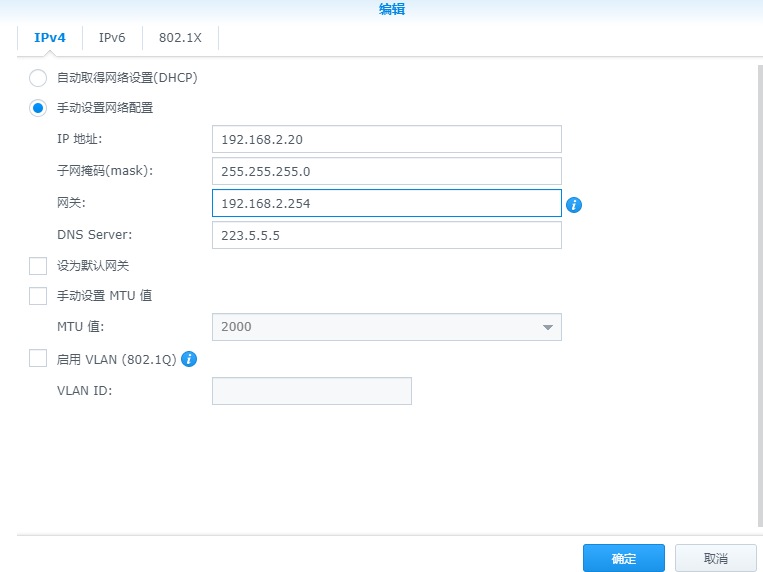
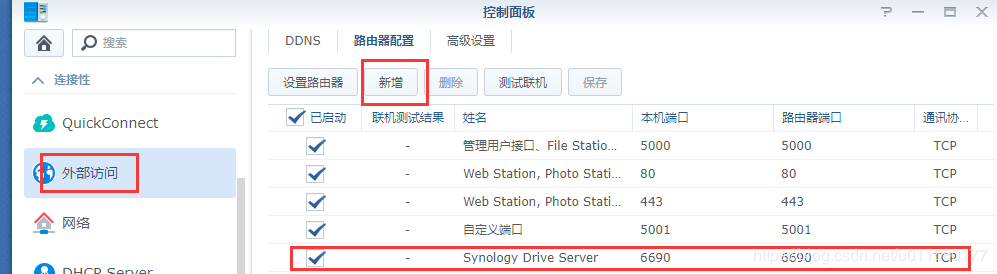
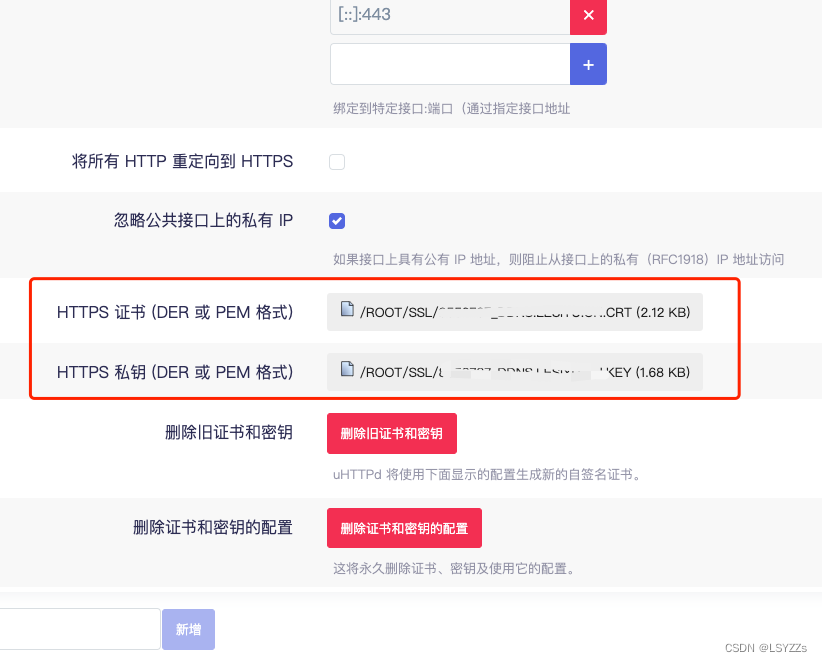
由于要配置上千条二级域名,域名注册商提供的二级域名记录条数有上限,不支持我们的需求。只能自己干了。
安装就 yum install bind* 即可。
关键的地方是配置。
第一个配置文件:/etc/named.conf
options { listen-on port 53 { 本机公网IP; }; listen-on-v6 port 53 { ::1; }; directory "/var/named"; dump-file "/var/named/data/cache_dump.db"; statistics-file "/var/named/data/named_stats.txt"; memstatistics-file "/var/named/data/named_mem_stats.txt"; recursing-file "/var/named/data/named.recursing"; secroots-file "/var/named/data/named.secroots"; allow-query { any; }; forwarders { 8.8.8.8;114.114.114.114; }; /* - If you are building an AUTHORITATIVE DNS server, do NOT enable recursion. - If you are building a RECURSIVE (caching) DNS server, you need to enable recursion. - If your recursive DNS server has a public IP address, you MUST enable access control to limit queries to your legitimate users. Failing to do so will cause your server to become part of large scale DNS amplification attacks. Implementing BCP38 within your network would greatly reduce such attack surface */ recursion yes; dnssec-enable yes; dnssec-validation yes; /* Path to ISC DLV key */ bindkeys-file "/etc/named.iscdlv.key"; managed-keys-directory "/var/named/dynamic"; pid-file "/run/named/named.pid"; session-keyfile "/run/named/session.key"; }; logging { channel default_debug { file "data/named.run"; severity dynamic; }; }; zone "." IN { type hint; file "named.ca"; }; include "/etc/named.rfc1912.zones"; include "/etc/named.root.key";options { listen-on port 53 { 本机公网IP; }; listen-on-v6 port 53 { ::1; }; directory "/var/named"; dump-file "/var/named/data/cache_dump.db"; statistics-file "/var/named/data/named_stats.txt"; memstatistics-file "/var/named/data/named_mem_stats.txt"; recursing-file "/var/named/data/named.recursing"; secroots-file "/var/named/data/named.secroots"; allow-query { any; }; forwarders { 8.8.8.8;114.114.114.114; }; /* - If you are building an AUTHORITATIVE DNS server, do NOT enable recursion. - If you are building a RECURSIVE (caching) DNS server, you need to enable recursion. - If your recursive DNS server has a public IP address, you MUST enable access control to limit queries to your legitimate users. Failing to do so will cause your server to become part of large scale DNS amplification attacks. Implementing BCP38 within your network would greatly reduce such attack surface */ recursion yes; dnssec-enable yes; dnssec-validation yes; /* Path to ISC DLV key */ bindkeys-file "/etc/named.iscdlv.key"; managed-keys-directory "/var/named/dynamic"; pid-file "/run/named/named.pid"; session-keyfile "/run/named/session.key"; }; logging { channel default_debug { file "data/named.run"; severity dynamic; }; }; zone "." IN { type hint; file "named.ca"; }; include "/etc/named.rfc1912.zones"; include "/etc/named.root.key";options { listen-on port 53 { 本机公网IP; }; listen-on-v6 port 53 { ::1; }; directory "/var/named"; dump-file "/var/named/data/cache_dump.db"; statistics-file "/var/named/data/named_stats.txt"; memstatistics-file "/var/named/data/named_mem_stats.txt"; recursing-file "/var/named/data/named.recursing"; secroots-file "/var/named/data/named.secroots"; allow-query { any; }; forwarders { 8.8.8.8;114.114.114.114; }; /* - If you are building an AUTHORITATIVE DNS server, do NOT enable recursion. - If you are building a RECURSIVE (caching) DNS server, you need to enable recursion. - If your recursive DNS server has a public IP address, you MUST enable access control to limit queries to your legitimate users. Failing to do so will cause your server to become part of large scale DNS amplification attacks. Implementing BCP38 within your network would greatly reduce such attack surface */ recursion yes; dnssec-enable yes; dnssec-validation yes; /* Path to ISC DLV key */ bindkeys-file "/etc/named.iscdlv.key"; managed-keys-directory "/var/named/dynamic"; pid-file "/run/named/named.pid"; session-keyfile "/run/named/session.key"; }; logging { channel default_debug { file "data/named.run"; severity dynamic; }; }; zone "." IN { type hint; file "named.ca"; }; include "/etc/named.rfc1912.zones"; include "/etc/named.root.key";
第二个配置文件:/etc/named.rfc1912.zones
zone "localhost.localdomain" IN { type master; file "named.localhost"; allow-update { none; }; }; zone "localhost" IN { type master; file "named.localhost"; allow-update { none; }; }; zone "example.cn" IN { type master; file "data/example.cn.zone"; allow-update { none; }; }; zone "example.in-addr.arpa" IN { type master; file "data/example.arpa.cn.zone"; allow-update { none; }; }; zone "0.in-addr.arpa" IN { type master; file "named.empty"; allow-update { none; }; };zone "localhost.localdomain" IN { type master; file "named.localhost"; allow-update { none; }; }; zone "localhost" IN { type master; file "named.localhost"; allow-update { none; }; }; zone "example.cn" IN { type master; file "data/example.cn.zone"; allow-update { none; }; }; zone "example.in-addr.arpa" IN { type master; file "data/example.arpa.cn.zone"; allow-update { none; }; }; zone "0.in-addr.arpa" IN { type master; file "named.empty"; allow-update { none; }; };zone "localhost.localdomain" IN { type master; file "named.localhost"; allow-update { none; }; }; zone "localhost" IN { type master; file "named.localhost"; allow-update { none; }; }; zone "example.cn" IN { type master; file "data/example.cn.zone"; allow-update { none; }; }; zone "example.in-addr.arpa" IN { type master; file "data/example.arpa.cn.zone"; allow-update { none; }; }; zone "0.in-addr.arpa" IN { type master; file "named.empty"; allow-update { none; }; };
第三个配置文件:/var/named/data/exampele.cn.zone
$TTL 1D @ IN SOA dns1.example.cn. admin.qq.com. ( 20190128 1D 1H 1W 3H ) IN NS dns1.example.cn. dns1.example.cn. IN A 本机公网IP test.example.cn. IN A 域名要指向的IP ftp.example.cn. IN A 域名要指向的IP abc.example.cn. IN A 域名要指向的IP zhang.example.cn. IN A 域名要指向的IP$TTL 1D @ IN SOA dns1.example.cn. admin.qq.com. ( 20190128 1D 1H 1W 3H ) IN NS dns1.example.cn. dns1.example.cn. IN A 本机公网IP test.example.cn. IN A 域名要指向的IP ftp.example.cn. IN A 域名要指向的IP abc.example.cn. IN A 域名要指向的IP zhang.example.cn. IN A 域名要指向的IP$TTL 1D @ IN SOA dns1.example.cn. admin.qq.com. ( 20190128 1D 1H 1W 3H ) IN NS dns1.example.cn. dns1.example.cn. IN A 本机公网IP test.example.cn. IN A 域名要指向的IP ftp.example.cn. IN A 域名要指向的IP abc.example.cn. IN A 域名要指向的IP zhang.example.cn. IN A 域名要指向的IP
第四个配置文件:/var/named/data/example.arpa.cn.zone
$TTL 1D @ IN SOA dns1.example.cn. dns1.qq.com. ( 20190128 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum NS dns1.example.cn. A 本机公网IP PTR test.example.cn. PTR ftp.example.cn. PTR abc.example.cn. PTR zhang.example.cn.$TTL 1D @ IN SOA dns1.example.cn. dns1.qq.com. ( 20190128 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum NS dns1.example.cn. A 本机公网IP PTR test.example.cn. PTR ftp.example.cn. PTR abc.example.cn. PTR zhang.example.cn.$TTL 1D @ IN SOA dns1.example.cn. dns1.qq.com. ( 20190128 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum NS dns1.example.cn. A 本机公网IP PTR test.example.cn. PTR ftp.example.cn. PTR abc.example.cn. PTR zhang.example.cn.
配置文件配置好之后, 用工具检查一下配置文件的语法是否正确:
检查主配置文件语法: named-checkconf /etc/named.conf 检查正向解析域的语法: named-checkzone example.cn /etc/named/zones/example.cn.zone 检查反向解析域的语法: named-checkzone example.in-addr.arpa /etc/named/zones/example.arpa.cn.zone检查主配置文件语法: named-checkconf /etc/named.conf 检查正向解析域的语法: named-checkzone example.cn /etc/named/zones/example.cn.zone 检查反向解析域的语法: named-checkzone example.in-addr.arpa /etc/named/zones/example.arpa.cn.zone检查主配置文件语法: named-checkconf /etc/named.conf 检查正向解析域的语法: named-checkzone example.cn /etc/named/zones/example.cn.zone 检查反向解析域的语法: named-checkzone example.in-addr.arpa /etc/named/zones/example.arpa.cn.zone
假如你的DNS服务器的IP地址为 :A.B.C.D
你还需要另外在注册一个域名, 比如:newgirl.com
你需要解析一个A记录为: mydns.newgirl.com 指向IP地址为 A.B.C.D 的服务器
然后把域名 example.cn 的DNS服务器设置为 : mydns.newgirl.com 即可。
最后启动服务:
systemctl start named.service
大功告成!
原文链接:https://blog.csdn.net/langeldep/article/details/86716024?ops_request_misc=&request_id=&biz_id=&utm_medium=distribute.pc_search_result.none-task-blog-2~blog~koosearch~default-17-86716024-null-null.268%5Ev1%5Ekoosearch&utm_term=%E9%BB%91%E7%BE%A4%E6%99%96%E3%80%81docker%E3%80%81%E5%AE%B9%E5%99%A8%E9%95%9C%E5%83%8F%E3%80%81%E5%9F%9F%E5%90%8D%E6%B3%A8%E5%86%8C%E3%80%81%E5%AE%9D%E5%A1%94%E3%80%81%E5%8F%8D%E5%90%91%E4%BB%A3%E7%90%86%E3%80%81nginx%E3%80%81frp%E3%80%81%E5%8A%A8%E6%80%81%E5%9F%9F%E5%90%8D%E8%A7%A3%E6%9E%90%E3%80%81NAS%E3%80%81%E7%BE%A4%E6%99%96%E3%80%81%E9%98%BF%E9%87%8C%E4%BA%91%E3%80%81%E5%9F%9F%E5%90%8D%E8%A7%A3%E6%9E%90%E3%80%81%E5%86%85%E7%BD%91%E7%A9%BF%E9%80%8F%E3%80%81ipv6%E3%80%81ddns%E3%80%81%E8%BD%BB%E9%87%8F%E7%BA%A7%E4%BA%91%E6%9C%8D%E5%8A%A1%E5%99%A8%E3%80%81%E9%93%81%E5%A8%81%E9%A9%AC%E3%80%81%E5%A8%81%E8%81%94%E9%80%9A%E3%80%81DSM%E3%80%81DSM6.0%E3%80%81%E7%BE%A4%E6%99%96nas%E3%80%81%E4%BA%91%E6%9C%8D%E5%8A%A1%E5%99%A8%E3%80%81%E8%9C%97%E7%89%9B%E6%98%9F%E9%99%85%E3%80%81