server {
listen 80;
#填写用于绑定KodExplorer的域名
server_name ;
#301跳转到https,如果不使用https协议可删除这行。
return 301 $request_uri;
location / {
#lanproxy转发http所对应的端口,Frp请使用自定义http监听端口
proxy_pass http://127.0.0.1:7890;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}
# 如果不使用https协议的下面部分可以略过。
server {
listen 443 ssl http2;
#填写用于绑定KodExplorer的域名
server_name ;
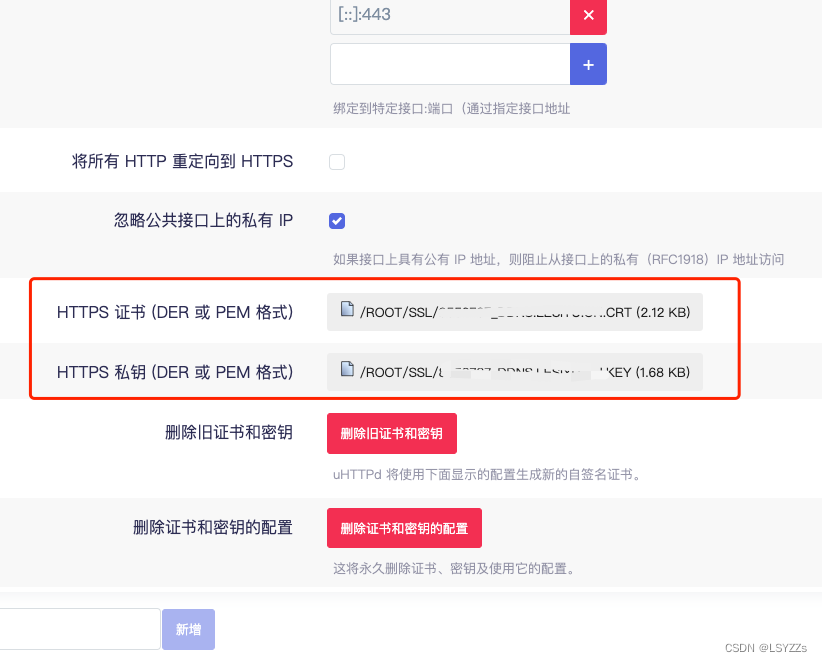
ssl_certificate /usr/local/nginx/fullchain.cer; #SSL证书路径
ssl_certificate_key /usr/local/nginx/domain.key; #证书密钥路径
ssl_stapling on;
ssl_stapling_verify on;
resolver 1.1.1.1 1.0.0.1 valid=300s;
resolver_timeout 5s;
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers ‘TLS13-AES-256-GCM-SHA384:TLS13-CHACHA20-POLY1305-SHA256:TLS13-AES-128-GCM-SHA256:TLS13-AES-128-CCM-8-SHA256:TLS13-AES-128-CCM-SHA256:EECDH+CHACHA20:EECDH+CHACHA20-draft:EECDH+ECDSA+AES128:EECDH+aRSA+AES128:EECDH+ECDSA+AES256:EECDH+aRSA+AES256:SSLCipherSuiteECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256;’;
ssl_prefer_server_ciphers on;
add_header X-Frame-Options ‘SAMEORIGIN’;
add_header X-XSS-Protection ‘1; mode=block’;
add_header X-Content-Type-Options ‘nosniff’;
location / {
proxy_ssl_server_name on;
#lanproxy转发https所对应的端口,Frp请使用自定义https监听端口
proxy_pass https://127.0.0.1:7430;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Remote-Port $remote_port;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_redirect off;
}
原文链接:http://www.360doc.com/content/20/1102/21/29497380_943761602.shtml