dns2tcp的github下载地址:https://github.com/alex-sector/dns2tcp
dns2tcp一般用于内网通过DNS隧道出公网网,比如通过dns2tcp搭建dns隧道绕过校园网认证登陆,但是如果借助ssh的反向代理或其他反向代理工具,也可以实现外网访问内网。
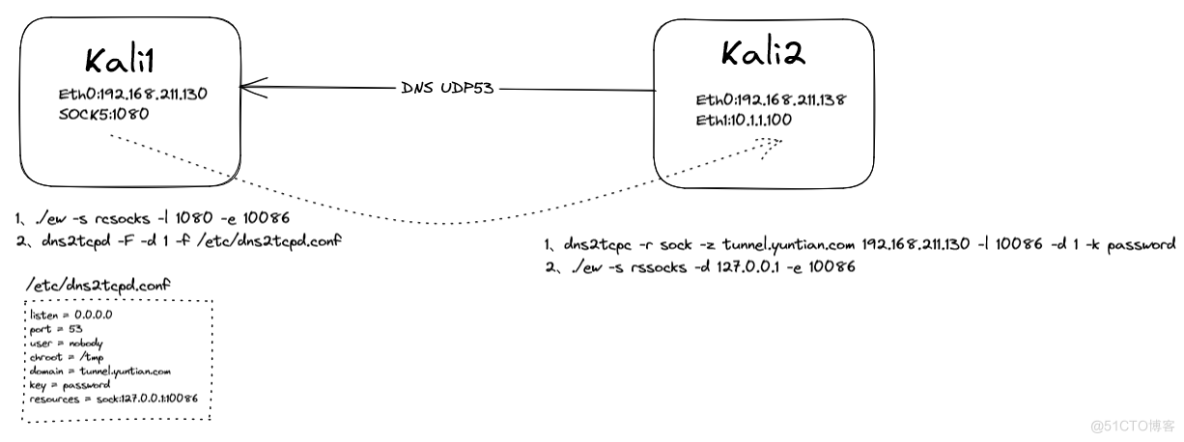
Kali自带dns2tcp,本文使用两台Kali进行测试,假定Kali1模拟具有公网IP的机器,做为dns2tcp的服务器端,Kali2模拟内网机器,做为dns2tcp的客户端,dns2tcp采用直连模式。
为了增加验证效果,Kali2配置了两块网卡,如下图所示:
Kali1(eth0:192.168.211.130)<—–DNS udp 53——–(eth0:192.168.211.138) Kali2 (eth1:100.1.1.1)
一、服务器端Kali1
┌──(root㉿kali)-[~/xll/ew/ew-master]
└─# ./ew -s rcsocks -l 1080 -e 10086
rcsocks 0.0.0.0:1080 <--[10000 usec]--> 0.0.0.0:10086
init cmd_server_for_rc here
start listen port here
┌──(root㉿kali)-[~]
└─# cat /etc/dns2tcpd.conf
listen = 0.0.0.0
port = 53
# If you change this value, also change the USER variable in /etc/default/dns2tcpd
user = nobody
chroot = /tmp
domain = tunnel.yuntian.com
key = password
resources = sock:127.0.0.1:10086
┌──(root㉿kali)-[~]
└─# dns2tcpd -F -d 1 -f /etc/dns2tcpd.conf
10:11:31 : Debug options.c:97 Add resource sock:127.0.0.1 port 10086
10:11:31 : Debug socket.c:54 Listening on 0.0.0.0:53 for domain tunnel.yuntian.com
Starting Server v0.5.2...
10:11:31 : Debug main.c:134 Chroot to /tmp
15:11:31 : Debug main.c:144 Change to user nobody
二、客户端Kali2
┌──(kali㉿kali)-[~]
└─$ dns2tcpc -z tunnel.yuntian.com 192.168.211.130 -k password
Available connection(s) :
sock
Note : Compression SEEMS available !
┌──(kali㉿kali)-[~]
└─$ dns2tcpc -r sock -z tunnel.yuntian.com 192.168.211.130 -l 10086 -d 1 -k password
debug level 1
Listening on port : 10086
┌──(kali㉿kali)-[~/xll/ew-master]
└─$ ./ew -s rssocks -d 127.0.0.1 -e 10086
rssocks 127.0.0.1:10086 <--[10000 usec]--> socks server
三、Kali1通过反向代理访问Kali2内网测试
┌──(root㉿kali)-[~]
└─# vi /etc/proxychains4.conf
socks5 127.0.0.1 1080
┌──(root㉿kali)-[~]
└─# proxychains ssh 100.1.1.1
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] Strict chain ... 127.0.0.1:1080 ... 100.1.1.1:22 ... OK
root@100.1.1.1's password:
Linux kali 5.14.0-kali2-amd64 #1 SMP Debian 5.14.9-2kali1 (2021-10-04) x86_64
The programs included with the Kali GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Kali GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Feb 2 09:45:11 2023 from 100.1.1.1
┏━(Message from Kali developers)
┃
┃ We have kept /usr/bin/python pointing to Python 2 for backwards
┃ compatibility. Learn how to change this and avoid this message:
┃ ⇒ https://www.kali.org/docs/general-use/python3-transition/
┃
┗━(Run: “touch ~/.hushlogin” to hide this message)
┌──(root💀kali)-[~]
└─# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.211.138 netmask 255.255.255.0 broadcast 192.168.211.255
inet6 fe80::20c:29ff:fe44:77a6 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:44:77:a6 txqueuelen 1000 (Ethernet)
RX packets 16553 bytes 6237802 (5.9 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 14238 bytes 1482063 (1.4 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 100.1.1.1 netmask 255.255.255.0 broadcast 100.1.1.255
ether 00:0c:29:44:77:b0 txqueuelen 1000 (Ethernet)
RX packets 506 bytes 44094 (43.0 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 172 bytes 58824 (57.4 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1000 (Local Loopback)
RX packets 1088 bytes 146863 (143.4 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1088 bytes 146863 (143.4 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
┌──(root㉿kali)-[~]
└─# netstat -an|grep 22
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 192.168.211.130:22 192.168.211.1:65069 ESTABLISHED
tcp 0 0 192.168.211.130:22 192.168.211.1:65197 ESTABLISHED
tcp 0 0 192.168.211.130:22 192.168.211.1:65004 ESTABLISHED
tcp6 0 0 :::22 :::* LISTEN
四、使用ssh反向代理实现同样的功能
##Kali1
┌──(root㉿kali)-[~]
└─# cat /etc/dns2tcpd.conf
listen = 0.0.0.0
port = 53
# If you change this value, also change the USER variable in /etc/default/dns2tcpd
user = nobody
chroot = /tmp
domain = tunnel.yuntian.com
key =password
resources = ssh:127.0.0.1:22
┌──(root㉿kali)-[~]
└─# dns2tcpd -F -d 1 -f /etc/dns2tcpd.conf
04:17:58 : Debug options.c:97 Add resource ssh:127.0.0.1 port 22
04:17:58 : Debug socket.c:54 Listening on 0.0.0.0:53 for domain tunnel.yuntian.com
Starting Server v0.5.2...
04:17:58 : Debug main.c:134 Chroot to /tmp
09:17:59 : Debug main.c:144 Change to user nobody
##Kali2
┌──(kali㉿kali)-[~]
└─$ dns2tcpc -r ssh -z tunnel.yuntian.com 192.168.211.130 -l 10022 -d 1 -k biyuntian
debug level 1
Listening on port : 10022
┌──(kali㉿kali)-[~]
└─$ ssh -NR 10086 kali@127.0.0.1 -p 10022 kali@127.0.0.1's password:
##Kali1
┌──(root㉿kali)-[~]
└─# netstat -an|grep 10086
tcp 0 0 127.0.0.1:10086 0.0.0.0:* LISTEN
tcp6 0 0 ::1:10086 :::* LISTEN
┌──(root㉿kali)-[~]
└─# proxychains ssh 10.1.1.100
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] Strict chain ... 127.0.0.1:10086 ... 10.1.1.100:22 ... OK
root@10.1.1.100's password:
┌──(root㉿kali)-[~]
└─# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.211.130 netmask 255.255.255.0 broadcast 192.168.211.255
inet6 fe80::20c:29ff:febe:fa59 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:be:fa:59 txqueuelen 1000 (Ethernet)
RX packets 2352 bytes 243255 (237.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 2002 bytes 281661 (275.0 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.1.1.100 netmask 255.255.255.0 broadcast 10.1.1.255
inet6 fe80::20c:29ff:febe:fa63 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:be:fa:63 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 16 bytes 1216 (1.1 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 405 bytes 67642 (66.0 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 405 bytes 67642 (66.0 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
原文链接:https://blog.51cto.com/u_333234/6035921
© 版权声明
声明📢本站内容均来自互联网,归原创作者所有,如有侵权必删除。
本站文章皆由CC-4.0协议发布,如无来源则为原创,转载请注明出处。
THE END