关闭防火墙和SELINUX
systemctl stop firewalld systemctl disable firewalld <span class="token function">sed</span> -i <span class="token string">'s/#SELINUX=enforcing/SELINUX=disabled/g'</span> /etc/selinux/configsystemctl stop firewalld systemctl disable firewalld <span class="token function">sed</span> -i <span class="token string">'s/#SELINUX=enforcing/SELINUX=disabled/g'</span> /etc/selinux/configsystemctl stop firewalld systemctl disable firewalld sed -i 's/#SELINUX=enforcing/SELINUX=disabled/g' /etc/selinux/config
安装etcd
yum安装
yum -y <span class="token function">install</span> etcdyum -y <span class="token function">install</span> etcdyum -y install etcd
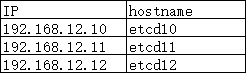
etcd10
<span class="token function">vi</span> /etc/etcd/etcd.conf <span class="token assign-left variable">ETCD_DATA_DIR</span><span class="token operator">=</span><span class="token string">"/var/lib/etcd/etcd10.etcd"</span> <span class="token assign-left variable">ETCD_WAL_DIR</span><span class="token operator">=</span><span class="token string">"/var/lib/etcd/etcd10/wal"</span> <span class="token assign-left variable">ETCD_LISTEN_PEER_URLS</span><span class="token operator">=</span><span class="token string">"http://192.168.12.10:2380"</span> <span class="token assign-left variable">ETCD_LISTEN_CLIENT_URLS</span><span class="token operator">=</span><span class="token string">"http://192.168.12.10:2379,http://127.0.0.1:2379"</span> <span class="token assign-left variable">ETCD_INITIAL_CLUSTER_TOKEN</span><span class="token operator">=</span><span class="token string">"etcd-cluster"</span> <span class="token assign-left variable">ETCD_NAME</span><span class="token operator">=</span><span class="token string">"etcd10"</span> <span class="token assign-left variable">ETCD_INITIAL_ADVERTISE_PEER_URLS</span><span class="token operator">=</span><span class="token string">"http://192.168.12.10:2380"</span> <span class="token assign-left variable">ETCD_ADVERTISE_CLIENT_URLS</span><span class="token operator">=</span><span class="token string">"http://192.168.12.10:2379"</span> <span class="token assign-left variable">ETCD_INITIAL_CLUSTER</span><span class="token operator">=</span><span class="token string">"etcd10=http://192.168.12.10:2380,etcd11=http://192.168.12.11:2380,etcd12=http://192.168.12.12:2380"</span><span class="token function">vi</span> /etc/etcd/etcd.conf <span class="token assign-left variable">ETCD_DATA_DIR</span><span class="token operator">=</span><span class="token string">"/var/lib/etcd/etcd10.etcd"</span> <span class="token assign-left variable">ETCD_WAL_DIR</span><span class="token operator">=</span><span class="token string">"/var/lib/etcd/etcd10/wal"</span> <span class="token assign-left variable">ETCD_LISTEN_PEER_URLS</span><span class="token operator">=</span><span class="token string">"http://192.168.12.10:2380"</span> <span class="token assign-left variable">ETCD_LISTEN_CLIENT_URLS</span><span class="token operator">=</span><span class="token string">"http://192.168.12.10:2379,http://127.0.0.1:2379"</span> <span class="token assign-left variable">ETCD_INITIAL_CLUSTER_TOKEN</span><span class="token operator">=</span><span class="token string">"etcd-cluster"</span> <span class="token assign-left variable">ETCD_NAME</span><span class="token operator">=</span><span class="token string">"etcd10"</span> <span class="token assign-left variable">ETCD_INITIAL_ADVERTISE_PEER_URLS</span><span class="token operator">=</span><span class="token string">"http://192.168.12.10:2380"</span> <span class="token assign-left variable">ETCD_ADVERTISE_CLIENT_URLS</span><span class="token operator">=</span><span class="token string">"http://192.168.12.10:2379"</span> <span class="token assign-left variable">ETCD_INITIAL_CLUSTER</span><span class="token operator">=</span><span class="token string">"etcd10=http://192.168.12.10:2380,etcd11=http://192.168.12.11:2380,etcd12=http://192.168.12.12:2380"</span>vi /etc/etcd/etcd.conf ETCD_DATA_DIR="/var/lib/etcd/etcd10.etcd" ETCD_WAL_DIR="/var/lib/etcd/etcd10/wal" ETCD_LISTEN_PEER_URLS="http://192.168.12.10:2380" ETCD_LISTEN_CLIENT_URLS="http://192.168.12.10:2379,http://127.0.0.1:2379" ETCD_INITIAL_CLUSTER_TOKEN="etcd-cluster" ETCD_NAME="etcd10" ETCD_INITIAL_ADVERTISE_PEER_URLS="http://192.168.12.10:2380" ETCD_ADVERTISE_CLIENT_URLS="http://192.168.12.10:2379" ETCD_INITIAL_CLUSTER="etcd10=http://192.168.12.10:2380,etcd11=http://192.168.12.11:2380,etcd12=http://192.168.12.12:2380"
etcd11
<span class="token assign-left variable">ETCD_DATA_DIR</span><span class="token operator">=</span><span class="token string">"/var/lib/etcd/etcd11.etcd"</span> <span class="token assign-left variable">ETCD_WAL_DIR</span><span class="token operator">=</span><span class="token string">"/var/lib/etcd/etcd11/wal"</span> <span class="token assign-left variable">ETCD_LISTEN_PEER_URLS</span><span class="token operator">=</span><span class="token string">"http://192.168.12.11:2380"</span> <span class="token assign-left variable">ETCD_LISTEN_CLIENT_URLS</span><span class="token operator">=</span><span class="token string">"http://192.168.12.11:2379,http://127.0.0.1:2379"</span> <span class="token assign-left variable">ETCD_NAME</span><span class="token operator">=</span><span class="token string">"etcd11"</span> <span class="token assign-left variable">ETCD_INITIAL_ADVERTISE_PEER_URLS</span><span class="token operator">=</span><span class="token string">"http://192.168.12.11:2380"</span> <span class="token assign-left variable">ETCD_INITIAL_CLUSTER</span><span class="token operator">=</span><span class="token string">"etcd10=http://192.168.12.10:2380,etcd11=http://192.168.12.11:2380,etcd12=http://192.168.12.12:2380"</span><span class="token assign-left variable">ETCD_DATA_DIR</span><span class="token operator">=</span><span class="token string">"/var/lib/etcd/etcd11.etcd"</span> <span class="token assign-left variable">ETCD_WAL_DIR</span><span class="token operator">=</span><span class="token string">"/var/lib/etcd/etcd11/wal"</span> <span class="token assign-left variable">ETCD_LISTEN_PEER_URLS</span><span class="token operator">=</span><span class="token string">"http://192.168.12.11:2380"</span> <span class="token assign-left variable">ETCD_LISTEN_CLIENT_URLS</span><span class="token operator">=</span><span class="token string">"http://192.168.12.11:2379,http://127.0.0.1:2379"</span> <span class="token assign-left variable">ETCD_NAME</span><span class="token operator">=</span><span class="token string">"etcd11"</span> <span class="token assign-left variable">ETCD_INITIAL_ADVERTISE_PEER_URLS</span><span class="token operator">=</span><span class="token string">"http://192.168.12.11:2380"</span> <span class="token assign-left variable">ETCD_INITIAL_CLUSTER</span><span class="token operator">=</span><span class="token string">"etcd10=http://192.168.12.10:2380,etcd11=http://192.168.12.11:2380,etcd12=http://192.168.12.12:2380"</span>ETCD_DATA_DIR="/var/lib/etcd/etcd11.etcd" ETCD_WAL_DIR="/var/lib/etcd/etcd11/wal" ETCD_LISTEN_PEER_URLS="http://192.168.12.11:2380" ETCD_LISTEN_CLIENT_URLS="http://192.168.12.11:2379,http://127.0.0.1:2379" ETCD_NAME="etcd11" ETCD_INITIAL_ADVERTISE_PEER_URLS="http://192.168.12.11:2380" ETCD_INITIAL_CLUSTER="etcd10=http://192.168.12.10:2380,etcd11=http://192.168.12.11:2380,etcd12=http://192.168.12.12:2380"
etcd12
<span class="token assign-left variable">ETCD_DATA_DIR</span><span class="token operator">=</span><span class="token string">"/var/lib/etcd/etcd12.etcd"</span> <span class="token assign-left variable">ETCD_WAL_DIR</span><span class="token operator">=</span><span class="token string">"/var/lib/etcd/etcd12/wal"</span> <span class="token assign-left variable">ETCD_LISTEN_PEER_URLS</span><span class="token operator">=</span><span class="token string">"http://192.168.12.12:2380"</span> <span class="token assign-left variable">ETCD_LISTEN_CLIENT_URLS</span><span class="token operator">=</span><span class="token string">"http://192.168.12.12:2379,http://127.0.0.1:2379"</span> <span class="token assign-left variable">ETCD_NAME</span><span class="token operator">=</span><span class="token string">"etcd12"</span> <span class="token assign-left variable">ETCD_INITIAL_ADVERTISE_PEER_URLS</span><span class="token operator">=</span><span class="token string">"http://192.168.12.12:2380"</span> <span class="token assign-left variable">ETCD_ADVERTISE_CLIENT_URLS</span><span class="token operator">=</span><span class="token string">"http://192.168.12.12:2379"</span> <span class="token assign-left variable">ETCD_INITIAL_CLUSTER</span><span class="token operator">=</span><span class="token string">"etcd10=http://192.168.12.10:2380,etcd11=http://192.168.12.11:2380,etcd12=http://192.168.12.12:2380"</span><span class="token assign-left variable">ETCD_DATA_DIR</span><span class="token operator">=</span><span class="token string">"/var/lib/etcd/etcd12.etcd"</span> <span class="token assign-left variable">ETCD_WAL_DIR</span><span class="token operator">=</span><span class="token string">"/var/lib/etcd/etcd12/wal"</span> <span class="token assign-left variable">ETCD_LISTEN_PEER_URLS</span><span class="token operator">=</span><span class="token string">"http://192.168.12.12:2380"</span> <span class="token assign-left variable">ETCD_LISTEN_CLIENT_URLS</span><span class="token operator">=</span><span class="token string">"http://192.168.12.12:2379,http://127.0.0.1:2379"</span> <span class="token assign-left variable">ETCD_NAME</span><span class="token operator">=</span><span class="token string">"etcd12"</span> <span class="token assign-left variable">ETCD_INITIAL_ADVERTISE_PEER_URLS</span><span class="token operator">=</span><span class="token string">"http://192.168.12.12:2380"</span> <span class="token assign-left variable">ETCD_ADVERTISE_CLIENT_URLS</span><span class="token operator">=</span><span class="token string">"http://192.168.12.12:2379"</span> <span class="token assign-left variable">ETCD_INITIAL_CLUSTER</span><span class="token operator">=</span><span class="token string">"etcd10=http://192.168.12.10:2380,etcd11=http://192.168.12.11:2380,etcd12=http://192.168.12.12:2380"</span>ETCD_DATA_DIR="/var/lib/etcd/etcd12.etcd" ETCD_WAL_DIR="/var/lib/etcd/etcd12/wal" ETCD_LISTEN_PEER_URLS="http://192.168.12.12:2380" ETCD_LISTEN_CLIENT_URLS="http://192.168.12.12:2379,http://127.0.0.1:2379" ETCD_NAME="etcd12" ETCD_INITIAL_ADVERTISE_PEER_URLS="http://192.168.12.12:2380" ETCD_ADVERTISE_CLIENT_URLS="http://192.168.12.12:2379" ETCD_INITIAL_CLUSTER="etcd10=http://192.168.12.10:2380,etcd11=http://192.168.12.11:2380,etcd12=http://192.168.12.12:2380"
name:etcd集群中的节点名,这里可以随意,可区分且不重复就行 listen-peer-urls:监听的用于节点之间通信的url,可监听多个,集群内部将通过这些url进行数据交互(如选举,数据同步等) initial-advertise-peer-urls:建议用于节点之间通信的url,节点间将以该值进行通信。 listen-client-urls:监听的用于客户端通信的url,同样可以监听多个。 advertise-client-urls:建议使用的客户端通信 url,该值用于 etcd 代理或 etcd 成员与 etcd 节点通信。 initial-cluster-token: etcd-cluster-1,节点的 token 值,设置该值后集群将生成唯一 id,并为每个节点也生成唯一 id,当使用相同配置文件再启动一个集群时,只要该 token 值不一样,etcd 集群就不会相互影响。 initial-cluster:也就是集群中所有的initial-advertise-peer-urls 的合集。 initial-cluster-state:new,新建集群的标志name:etcd集群中的节点名,这里可以随意,可区分且不重复就行 listen-peer-urls:监听的用于节点之间通信的url,可监听多个,集群内部将通过这些url进行数据交互(如选举,数据同步等) initial-advertise-peer-urls:建议用于节点之间通信的url,节点间将以该值进行通信。 listen-client-urls:监听的用于客户端通信的url,同样可以监听多个。 advertise-client-urls:建议使用的客户端通信 url,该值用于 etcd 代理或 etcd 成员与 etcd 节点通信。 initial-cluster-token: etcd-cluster-1,节点的 token 值,设置该值后集群将生成唯一 id,并为每个节点也生成唯一 id,当使用相同配置文件再启动一个集群时,只要该 token 值不一样,etcd 集群就不会相互影响。 initial-cluster:也就是集群中所有的initial-advertise-peer-urls 的合集。 initial-cluster-state:new,新建集群的标志name:etcd集群中的节点名,这里可以随意,可区分且不重复就行 listen-peer-urls:监听的用于节点之间通信的url,可监听多个,集群内部将通过这些url进行数据交互(如选举,数据同步等) initial-advertise-peer-urls:建议用于节点之间通信的url,节点间将以该值进行通信。 listen-client-urls:监听的用于客户端通信的url,同样可以监听多个。 advertise-client-urls:建议使用的客户端通信 url,该值用于 etcd 代理或 etcd 成员与 etcd 节点通信。 initial-cluster-token: etcd-cluster-1,节点的 token 值,设置该值后集群将生成唯一 id,并为每个节点也生成唯一 id,当使用相同配置文件再启动一个集群时,只要该 token 值不一样,etcd 集群就不会相互影响。 initial-cluster:也就是集群中所有的initial-advertise-peer-urls 的合集。 initial-cluster-state:new,新建集群的标志参考:https://etcd.io/docs/v3.5/op-guide/configuration/
配置API版本为3,默认为2
<span class="token function">vi</span> /etc/profile <span class="token builtin class-name">export</span> <span class="token assign-left variable">ETCDCTL_API</span><span class="token operator">=</span><span class="token number">3</span> <span class="token builtin class-name">source</span> /etc/profile<span class="token function">vi</span> /etc/profile <span class="token builtin class-name">export</span> <span class="token assign-left variable">ETCDCTL_API</span><span class="token operator">=</span><span class="token number">3</span> <span class="token builtin class-name">source</span> /etc/profilevi /etc/profile export ETCDCTL_API=3 source /etc/profile
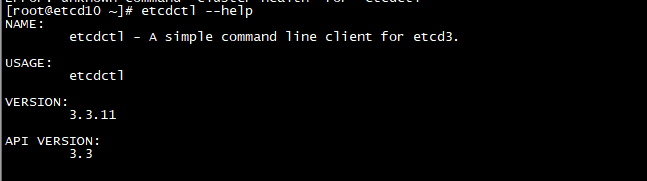
常见使用命令
设置环境变量,便于查询
<span class="token builtin class-name">export</span> <span class="token assign-left variable">ETCDCTL_ENDPOINTS</span><span class="token operator">=</span><span class="token string">"https://192.168.12.10:2379,https://192.168.12.11:2379,https://192.168.12.12:2379"</span><span class="token builtin class-name">export</span> <span class="token assign-left variable">ETCDCTL_ENDPOINTS</span><span class="token operator">=</span><span class="token string">"https://192.168.12.10:2379,https://192.168.12.11:2379,https://192.168.12.12:2379"</span>export ETCDCTL_ENDPOINTS="https://192.168.12.10:2379,https://192.168.12.11:2379,https://192.168.12.12:2379"
etcdctl endpoint health etcdctl member list etcdctl put d1 <span class="token string">"hello world"</span> etcdctl put d1/d2 <span class="token string">"test 2020"</span> etcdctl get d1 etcdctl del d1etcdctl endpoint health etcdctl member list etcdctl put d1 <span class="token string">"hello world"</span> etcdctl put d1/d2 <span class="token string">"test 2020"</span> etcdctl get d1 etcdctl del d1etcdctl endpoint health etcdctl member list etcdctl put d1 "hello world" etcdctl put d1/d2 "test 2020" etcdctl get d1 etcdctl del d1
SSL/TLS安全
- cfssl:cfssl 是 CloudFlare 的 PKI/TLS 利器。 它既是命令行工具,又可以用于签名,验证和捆绑 TLS 证书的 HTTP API 服务器,环境构建方面需要 Go 1.12+
- cfssljson:从 cfssl 获取 JSON 输出,并将证书、密钥、CSR和 bundle 写入指定位置
cfssl和cfssljson都是基于go语言,只有一个二进制程序,无任何依赖,真正开箱即用
下载使用
<span class="token function">wget</span> https://pkg.cfssl.org/R1.2/cfssl_linux-amd64 https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64 <span class="token function">mv</span> cfssl_linux-amd64 /usr/local/bin/cfssl <span class="token function">mv</span> cfssljson_linux-amd64 /usr/local/bin/cfssljson <span class="token function">chmod</span> <span class="token number">755</span> /usr/local/bin/cfssl /usr/local/bin/cfssljson cfssl version<span class="token function">wget</span> https://pkg.cfssl.org/R1.2/cfssl_linux-amd64 https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64 <span class="token function">mv</span> cfssl_linux-amd64 /usr/local/bin/cfssl <span class="token function">mv</span> cfssljson_linux-amd64 /usr/local/bin/cfssljson <span class="token function">chmod</span> <span class="token number">755</span> /usr/local/bin/cfssl /usr/local/bin/cfssljson cfssl versionwget https://pkg.cfssl.org/R1.2/cfssl_linux-amd64 https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64 mv cfssl_linux-amd64 /usr/local/bin/cfssl mv cfssljson_linux-amd64 /usr/local/bin/cfssljson chmod 755 /usr/local/bin/cfssl /usr/local/bin/cfssljson cfssl version
Linux内部使用的证书类型
- client certificate: 用于服务端认证客户端,例如etcdctl、etcd proxy、fleetctl、docker客户端
- server certificate: 服务端使用,客户端以此验证服务端身份,例如docker服务端、kube-apiserver
- peer certificate: 双向证书,用于etcd集群成员间通信
配置 CA 并创建 TLS 证书
<span class="token function">mkdir</span> -p /opt/etcd/ssl <span class="token builtin class-name">cd</span> /opt/etcd/ssl <span class="token function">vi</span> ca-config.json <span class="token punctuation">{<!-- --></span> <span class="token string">"signing"</span><span class="token builtin class-name">:</span> <span class="token punctuation">{<!-- --></span> <span class="token string">"default"</span><span class="token builtin class-name">:</span> <span class="token punctuation">{<!-- --></span> <span class="token string">"expiry"</span><span class="token builtin class-name">:</span> <span class="token string">"43800h"</span> <span class="token punctuation">}</span>, <span class="token string">"profiles"</span><span class="token builtin class-name">:</span> <span class="token punctuation">{<!-- --></span> <span class="token string">"server"</span><span class="token builtin class-name">:</span> <span class="token punctuation">{<!-- --></span> <span class="token string">"expiry"</span><span class="token builtin class-name">:</span> <span class="token string">"43800h"</span>, <span class="token string">"usages"</span><span class="token builtin class-name">:</span> <span class="token punctuation">[</span> <span class="token string">"signing"</span>, <span class="token string">"key encipherment"</span>, <span class="token string">"client auth"</span>, <span class="token string">"server auth"</span> <span class="token punctuation">]</span> <span class="token punctuation">}</span> <span class="token punctuation">}</span> <span class="token punctuation">}</span> <span class="token punctuation">}</span> <span class="token function">vi</span> ca-csr.json <span class="token punctuation">{<!-- --></span> <span class="token string">"CN"</span><span class="token builtin class-name">:</span> <span class="token string">"My own CA"</span>, <span class="token string">"key"</span><span class="token builtin class-name">:</span> <span class="token punctuation">{<!-- --></span> <span class="token string">"algo"</span><span class="token builtin class-name">:</span> <span class="token string">"rsa"</span>, <span class="token string">"size"</span><span class="token builtin class-name">:</span> <span class="token number">2048</span> <span class="token punctuation">}</span>, <span class="token string">"names"</span><span class="token builtin class-name">:</span> <span class="token punctuation">[</span> <span class="token punctuation">{<!-- --></span> <span class="token string">"C"</span><span class="token builtin class-name">:</span> <span class="token string">"CN"</span>, <span class="token string">"L"</span><span class="token builtin class-name">:</span> <span class="token string">"SHANGHAI"</span>, <span class="token string">"O"</span><span class="token builtin class-name">:</span> <span class="token string">"SH"</span>, <span class="token string">"ST"</span><span class="token builtin class-name">:</span> <span class="token string">"SHANGHAI"</span>, <span class="token string">"OU"</span><span class="token builtin class-name">:</span> <span class="token string">"SH-HD"</span> <span class="token punctuation">}</span> <span class="token punctuation">]</span> <span class="token punctuation">}</span> cfssl gencert -initca ca-csr.json <span class="token operator">|</span> cfssljson -bare ca -<span class="token function">mkdir</span> -p /opt/etcd/ssl <span class="token builtin class-name">cd</span> /opt/etcd/ssl <span class="token function">vi</span> ca-config.json <span class="token punctuation">{<!-- --></span> <span class="token string">"signing"</span><span class="token builtin class-name">:</span> <span class="token punctuation">{<!-- --></span> <span class="token string">"default"</span><span class="token builtin class-name">:</span> <span class="token punctuation">{<!-- --></span> <span class="token string">"expiry"</span><span class="token builtin class-name">:</span> <span class="token string">"43800h"</span> <span class="token punctuation">}</span>, <span class="token string">"profiles"</span><span class="token builtin class-name">:</span> <span class="token punctuation">{<!-- --></span> <span class="token string">"server"</span><span class="token builtin class-name">:</span> <span class="token punctuation">{<!-- --></span> <span class="token string">"expiry"</span><span class="token builtin class-name">:</span> <span class="token string">"43800h"</span>, <span class="token string">"usages"</span><span class="token builtin class-name">:</span> <span class="token punctuation">[</span> <span class="token string">"signing"</span>, <span class="token string">"key encipherment"</span>, <span class="token string">"client auth"</span>, <span class="token string">"server auth"</span> <span class="token punctuation">]</span> <span class="token punctuation">}</span> <span class="token punctuation">}</span> <span class="token punctuation">}</span> <span class="token punctuation">}</span> <span class="token function">vi</span> ca-csr.json <span class="token punctuation">{<!-- --></span> <span class="token string">"CN"</span><span class="token builtin class-name">:</span> <span class="token string">"My own CA"</span>, <span class="token string">"key"</span><span class="token builtin class-name">:</span> <span class="token punctuation">{<!-- --></span> <span class="token string">"algo"</span><span class="token builtin class-name">:</span> <span class="token string">"rsa"</span>, <span class="token string">"size"</span><span class="token builtin class-name">:</span> <span class="token number">2048</span> <span class="token punctuation">}</span>, <span class="token string">"names"</span><span class="token builtin class-name">:</span> <span class="token punctuation">[</span> <span class="token punctuation">{<!-- --></span> <span class="token string">"C"</span><span class="token builtin class-name">:</span> <span class="token string">"CN"</span>, <span class="token string">"L"</span><span class="token builtin class-name">:</span> <span class="token string">"SHANGHAI"</span>, <span class="token string">"O"</span><span class="token builtin class-name">:</span> <span class="token string">"SH"</span>, <span class="token string">"ST"</span><span class="token builtin class-name">:</span> <span class="token string">"SHANGHAI"</span>, <span class="token string">"OU"</span><span class="token builtin class-name">:</span> <span class="token string">"SH-HD"</span> <span class="token punctuation">}</span> <span class="token punctuation">]</span> <span class="token punctuation">}</span> cfssl gencert -initca ca-csr.json <span class="token operator">|</span> cfssljson -bare ca -mkdir -p /opt/etcd/ssl cd /opt/etcd/ssl vi ca-config.json { "signing": { "default": { "expiry": "43800h" }, "profiles": { "server": { "expiry": "43800h", "usages": [ "signing", "key encipherment", "client auth", "server auth" ] } } } } vi ca-csr.json { "CN": "My own CA", "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "L": "SHANGHAI", "O": "SH", "ST": "SHANGHAI", "OU": "SH-HD" } ] } cfssl gencert -initca ca-csr.json | cfssljson -bare ca -
ST=省/L=市/O=组织名/OU=组织单位/C=国家
配置 server证书
<span class="token function">vi</span> server.json <span class="token punctuation">{<!-- --></span> <span class="token string">"CN"</span><span class="token builtin class-name">:</span> <span class="token string">"etcd"</span>, <span class="token string">"hosts"</span><span class="token builtin class-name">:</span> <span class="token punctuation">[</span> <span class="token string">"192.168.12.10"</span>, <span class="token string">"192.168.12.11"</span>, <span class="token string">"192.168.12.12"</span> <span class="token punctuation">]</span>, <span class="token string">"key"</span><span class="token builtin class-name">:</span> <span class="token punctuation">{<!-- --></span> <span class="token string">"algo"</span><span class="token builtin class-name">:</span> <span class="token string">"rsa"</span>, <span class="token string">"size"</span><span class="token builtin class-name">:</span> <span class="token number">2048</span> <span class="token punctuation">}</span>, <span class="token string">"names"</span><span class="token builtin class-name">:</span> <span class="token punctuation">[</span> <span class="token punctuation">{<!-- --></span> <span class="token string">"C"</span><span class="token builtin class-name">:</span> <span class="token string">"CN"</span>, <span class="token string">"L"</span><span class="token builtin class-name">:</span> <span class="token string">"SHANGHAI"</span>, <span class="token string">"ST"</span><span class="token builtin class-name">:</span> <span class="token string">"SHANGHAI"</span> <span class="token punctuation">}</span> <span class="token punctuation">]</span> <span class="token punctuation">}</span> cfssl gencert -ca<span class="token operator">=</span>ca.pem -ca-key<span class="token operator">=</span>ca-key.pem -config<span class="token operator">=</span>ca-config.json -profile<span class="token operator">=</span>peer server.json <span class="token operator">|</span> cfssljson -bare server<span class="token function">vi</span> server.json <span class="token punctuation">{<!-- --></span> <span class="token string">"CN"</span><span class="token builtin class-name">:</span> <span class="token string">"etcd"</span>, <span class="token string">"hosts"</span><span class="token builtin class-name">:</span> <span class="token punctuation">[</span> <span class="token string">"192.168.12.10"</span>, <span class="token string">"192.168.12.11"</span>, <span class="token string">"192.168.12.12"</span> <span class="token punctuation">]</span>, <span class="token string">"key"</span><span class="token builtin class-name">:</span> <span class="token punctuation">{<!-- --></span> <span class="token string">"algo"</span><span class="token builtin class-name">:</span> <span class="token string">"rsa"</span>, <span class="token string">"size"</span><span class="token builtin class-name">:</span> <span class="token number">2048</span> <span class="token punctuation">}</span>, <span class="token string">"names"</span><span class="token builtin class-name">:</span> <span class="token punctuation">[</span> <span class="token punctuation">{<!-- --></span> <span class="token string">"C"</span><span class="token builtin class-name">:</span> <span class="token string">"CN"</span>, <span class="token string">"L"</span><span class="token builtin class-name">:</span> <span class="token string">"SHANGHAI"</span>, <span class="token string">"ST"</span><span class="token builtin class-name">:</span> <span class="token string">"SHANGHAI"</span> <span class="token punctuation">}</span> <span class="token punctuation">]</span> <span class="token punctuation">}</span> cfssl gencert -ca<span class="token operator">=</span>ca.pem -ca-key<span class="token operator">=</span>ca-key.pem -config<span class="token operator">=</span>ca-config.json -profile<span class="token operator">=</span>peer server.json <span class="token operator">|</span> cfssljson -bare servervi server.json { "CN": "etcd", "hosts": [ "192.168.12.10", "192.168.12.11", "192.168.12.12" ], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "L": "SHANGHAI", "ST": "SHANGHAI" } ] } cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=peer server.json | cfssljson -bare server
ca-csr.json: CSR的JSON设定文件
ca.csr: 证书签名请求文件
ca-key.pem:CA私钥
ca.pem: CA证书
其他配置
<span class="token builtin class-name">cd</span> /opt/etcd/ssl <span class="token function">chmod</span> <span class="token number">755</span> * <span class="token function">scp</span> /opt/etcd/ssl/* root@192.168.12.11:/opt/etcd/ssl <span class="token function">scp</span> /opt/etcd/ssl/* root@192.168.12.12:/opt/etcd/ssl <span class="token number">1</span>、etcd配置文件http改成https <span class="token function">sed</span> -i <span class="token string">'s/http/https/g'</span> /etc/etcd/etcd.conf <span class="token number">2</span>、配置启动Security <span class="token assign-left variable">ETCD_CERT_FILE</span><span class="token operator">=</span><span class="token string">"/opt/etcd/ssl/server.pem"</span> <span class="token assign-left variable">ETCD_KEY_FILE</span><span class="token operator">=</span><span class="token string">"/opt/etcd/ssl/server-key.pem"</span> <span class="token assign-left variable">ETCD_CLIENT_CERT_AUTH</span><span class="token operator">=</span><span class="token string">"true"</span> <span class="token assign-left variable">ETCD_TRUSTED_CA_FILE</span><span class="token operator">=</span><span class="token string">"/opt/etcd/ssl/ca.pem"</span> <span class="token assign-left variable">ETCD_PEER_CERT_FILE</span><span class="token operator">=</span><span class="token string">"/opt/etcd/ssl/server.pem"</span> <span class="token assign-left variable">ETCD_PEER_KEY_FILE</span><span class="token operator">=</span><span class="token string">"/opt/etcd/ssl/server-key.pem"</span> <span class="token assign-left variable">ETCD_PEER_CLIENT_CERT_AUTH</span><span class="token operator">=</span><span class="token string">"true"</span> <span class="token assign-left variable">ETCD_PEER_TRUSTED_CA_FILE</span><span class="token operator">=</span><span class="token string">"/opt/etcd/ssl/ca.pem"</span> systemctl restart etcd<span class="token builtin class-name">cd</span> /opt/etcd/ssl <span class="token function">chmod</span> <span class="token number">755</span> * <span class="token function">scp</span> /opt/etcd/ssl/* root@192.168.12.11:/opt/etcd/ssl <span class="token function">scp</span> /opt/etcd/ssl/* root@192.168.12.12:/opt/etcd/ssl <span class="token number">1</span>、etcd配置文件http改成https <span class="token function">sed</span> -i <span class="token string">'s/http/https/g'</span> /etc/etcd/etcd.conf <span class="token number">2</span>、配置启动Security <span class="token assign-left variable">ETCD_CERT_FILE</span><span class="token operator">=</span><span class="token string">"/opt/etcd/ssl/server.pem"</span> <span class="token assign-left variable">ETCD_KEY_FILE</span><span class="token operator">=</span><span class="token string">"/opt/etcd/ssl/server-key.pem"</span> <span class="token assign-left variable">ETCD_CLIENT_CERT_AUTH</span><span class="token operator">=</span><span class="token string">"true"</span> <span class="token assign-left variable">ETCD_TRUSTED_CA_FILE</span><span class="token operator">=</span><span class="token string">"/opt/etcd/ssl/ca.pem"</span> <span class="token assign-left variable">ETCD_PEER_CERT_FILE</span><span class="token operator">=</span><span class="token string">"/opt/etcd/ssl/server.pem"</span> <span class="token assign-left variable">ETCD_PEER_KEY_FILE</span><span class="token operator">=</span><span class="token string">"/opt/etcd/ssl/server-key.pem"</span> <span class="token assign-left variable">ETCD_PEER_CLIENT_CERT_AUTH</span><span class="token operator">=</span><span class="token string">"true"</span> <span class="token assign-left variable">ETCD_PEER_TRUSTED_CA_FILE</span><span class="token operator">=</span><span class="token string">"/opt/etcd/ssl/ca.pem"</span> systemctl restart etcdcd /opt/etcd/ssl chmod 755 * scp /opt/etcd/ssl/* root@192.168.12.11:/opt/etcd/ssl scp /opt/etcd/ssl/* root@192.168.12.12:/opt/etcd/ssl 1、etcd配置文件http改成https sed -i 's/http/https/g' /etc/etcd/etcd.conf 2、配置启动Security ETCD_CERT_FILE="/opt/etcd/ssl/server.pem" ETCD_KEY_FILE="/opt/etcd/ssl/server-key.pem" ETCD_CLIENT_CERT_AUTH="true" ETCD_TRUSTED_CA_FILE="/opt/etcd/ssl/ca.pem" ETCD_PEER_CERT_FILE="/opt/etcd/ssl/server.pem" ETCD_PEER_KEY_FILE="/opt/etcd/ssl/server-key.pem" ETCD_PEER_CLIENT_CERT_AUTH="true" ETCD_PEER_TRUSTED_CA_FILE="/opt/etcd/ssl/ca.pem" systemctl restart etcd
测试访问
配置环境变量: <span class="token builtin class-name">export</span> <span class="token assign-left variable">ETCDCTL_ENDPOINTS</span><span class="token operator">=</span><span class="token string">"https://192.168.12.10:2379,https://192.168.12.11:2379,https://192.168.12.12:2379"</span> <span class="token builtin class-name">export</span> <span class="token assign-left variable">ETCDCTL_CACERT</span><span class="token operator">=</span><span class="token string">"/etc/etcd/ssl/ca.pem"</span> <span class="token builtin class-name">export</span> <span class="token assign-left variable">ETCDCTL_CERT</span><span class="token operator">=</span><span class="token string">"/etc/etcd/ssl/server.pem"</span> <span class="token builtin class-name">export</span> <span class="token assign-left variable">ETCDCTL_KEY</span><span class="token operator">=</span><span class="token string">"/etc/etcd/ssl/server-key.pem"</span> etcdctl endpoint health配置环境变量: <span class="token builtin class-name">export</span> <span class="token assign-left variable">ETCDCTL_ENDPOINTS</span><span class="token operator">=</span><span class="token string">"https://192.168.12.10:2379,https://192.168.12.11:2379,https://192.168.12.12:2379"</span> <span class="token builtin class-name">export</span> <span class="token assign-left variable">ETCDCTL_CACERT</span><span class="token operator">=</span><span class="token string">"/etc/etcd/ssl/ca.pem"</span> <span class="token builtin class-name">export</span> <span class="token assign-left variable">ETCDCTL_CERT</span><span class="token operator">=</span><span class="token string">"/etc/etcd/ssl/server.pem"</span> <span class="token builtin class-name">export</span> <span class="token assign-left variable">ETCDCTL_KEY</span><span class="token operator">=</span><span class="token string">"/etc/etcd/ssl/server-key.pem"</span> etcdctl endpoint health配置环境变量: export ETCDCTL_ENDPOINTS="https://192.168.12.10:2379,https://192.168.12.11:2379,https://192.168.12.12:2379" export ETCDCTL_CACERT="/etc/etcd/ssl/ca.pem" export ETCDCTL_CERT="/etc/etcd/ssl/server.pem" export ETCDCTL_KEY="/etc/etcd/ssl/server-key.pem" etcdctl endpoint health
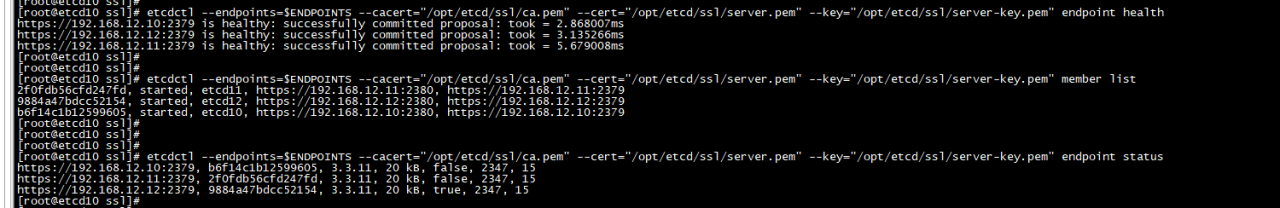
参考:https://github.com/coreos/docs/blob/master/os/generate-self-signed-certificates.md
参考:https://zhuanlan.zhihu.com/p/148175839
原文链接:https://blog.csdn.net/yangshihuz/article/details/111873186
© 版权声明
声明📢本站内容均来自互联网,归原创作者所有,如有侵权必删除。
本站文章皆由CC-4.0协议发布,如无来源则为原创,转载请注明出处。
THE END