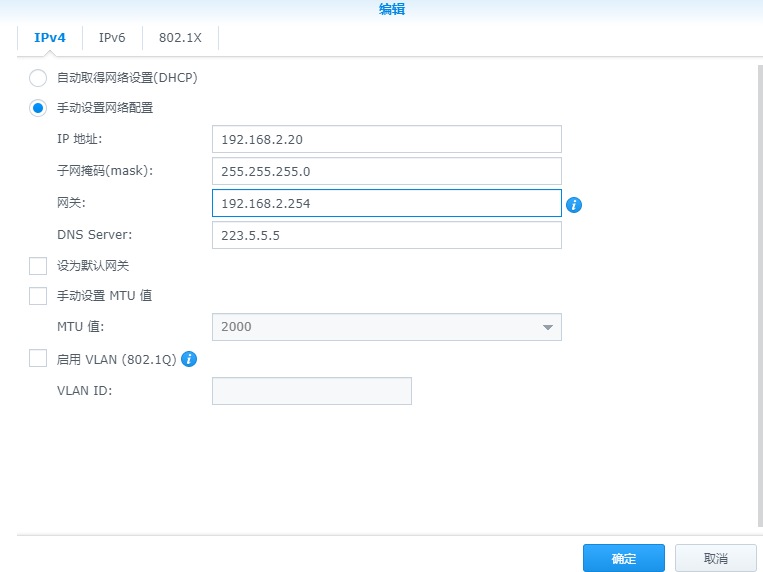
两个网络采用 ping测试方式,192.168.1.0/24和1.1.1.0/24两个内网可以相互访问。
2 debug flow产看数据流
从 192.168.1.111 ping 1.1.1.3
NGFW1
dia deb flow
id=13 trace_id=6 func=print_pkt_detail line=4316 msg="vd-root received a packet(proto=1, 192.168.1.111:1->1.1.1.3:8) from internal. code=8, type=0, id=1, seq=41."
id=13 trace_id=6 func=resolve_ip_tuple_fast line=4375 msg="Find an existing session, id-0000071f, original direction"
id=13 trace_id=6 func=ipsecdev_hard_start_xmit line=121 msg="enter IPsec interface-vpn"
id=13 trace_id=6 func=ipsec_output_finish line=232 msg="send to 192.168.118.1 via intf-wan1"
id=13 trace_id=6 func=esp_output4 line=889 msg="encrypting, and send to 1.1.1.2 with source 192.168.118.14"
NGFW2
id=25823 trace_id=5 func=print_pkt_detail line=4316 msg="vd-root received a packet(proto=1, 192.168.1.111:1->1.1.1.3:8) from vpn. code=8, type=0, id=1, seq=44."id=25823 trace_id=5 func=init_ip_session_common line=4472 msg="allocate a new session-00000087"
id=25823 trace_id=5 func=vf_ip4_route_input line=1600 msg="find a route: flags=00000000 gw-1.1.1.3 via wan1"
id=25823 trace_id=5 func=fw_forward_handler line=687 msg="Allowed by Policy-3:"
id=25823 trace_id=6 func=print_pkt_detail line=4316 msg="vd-root received a packet(proto=1, 1.1.1.3:1->192.168.1.111:0) from wan1. code=0, type=0, id=1, seq=44."
id=25823 trace_id=6 func=resolve_ip_tuple_fast line=4375 msg="Find an existing session, id-00000087, reply direction"
id=25823 trace_id=6 func=vf_ip4_route_input line=1600 msg="find a route: flags=00000000 gw-192.168.1.111 via vpn"
id=25823 trace_id=6 func=ipsecdev_hard_start_xmit line=121 msg="enter IPsec interface-vpn"
id=25823 trace_id=6 func=ipsec_output_finish line=232 msg="send to 1.1.1.1 via intf-wan1"
id=25823 trace_id=6 func=esp_output4 line=889 msg="encrypting, and send to 192.168.118.14 with source 1.1.1.2"
从 1.1.1.3 ping 192.168.1.200
NGFW2:
id=25823 trace_id=23 func=print_pkt_detail line=4316 msg="vd-root received a packet(proto=1, 1.1.1.3:1024->192.168.1.200:8) from wan1. code=8, type=0, id=1024, seq=0."
id=25823 trace_id=23 func=init_ip_session_common line=4472 msg="allocate a new session-00000090"
id=25823 trace_id=23 func=vf_ip4_route_input line=1600 msg="find a route: flags=00000000 gw-192.168.1.200 via vpn"
id=25823 trace_id=23 func=fw_forward_handler line=687 msg="Allowed by Policy-2:"
id=25823 trace_id=23 func=ipsecdev_hard_start_xmit line=121 msg="enter IPsec interface-vpn"
id=25823 trace_id=23 func=ipsec_output_finish line=232 msg="send to 1.1.1.1 via intf-wan1"
id=25823 trace_id=23 func=esp_output4 line=889 msg="encrypting, and send to 192.168.118.14 with source 1.1.1.2"
原文链接:https://blog.csdn.net/weixin_57099902/article/details/133345476